What is Configuration Drift?
Configuration drift occurs when the actual state of your Kubernetes resources no longer matches the desired state defined in your IaC configuration files or manifests. Kubernetes follows a declarative approach where you specify how resources should be configured, and the cluster's control plane makes sure that this configuration is applied. Tools like Terraform and Kubernetes work together to define and manage cluster resources while ensuring they stay aligned with the desired state. However, changes made outside of these workflows can result in differences between what is defined and what is running in the cluster.
Drift can occur in several ways. For example, a deployment defined for two replicas in your IaC configuration files might end up running a different number due to changes made through automation scripts during scaling operations. Similarly, a service initially configured as ClusterIP might be changed to LoadBalancer during a debugging session, leading to a mismatch between the defined and actual configurations.
Now, these changes disrupt the consistency in cluster configurations and make it difficult to maintain a reliable environment. Without alignment between the actual and defined states, troubleshooting becomes difficult because the configuration files no longer provide accurate information about the cluster.
Addressing configuration drift is important for maintaining a Kubernetes cluster that is stable, secure, and manageable. Keeping the actual state aligned with the desired state ensures predictable operations and also reduces security risks across your infrastructure.
Causes of Drift in Kubernetes
Now, to deal with configuration drift, it’s important to understand what causes it. Drift doesn’t happen on its own; it’s usually the result of actions or events that change the state of Kubernetes resources outside of the workflows defined in your configuration files.
There are several common reasons why drift occurs in Kubernetes. These include actions taken by users, automatic updates by the cluster, or problems with the resources themselves. Here are the main causes:
Changes made using CLI or scripts
When resources in a Kubernetes cluster are updated directly using CLI commands like kubectl scale deployment nginx-deployment --replicas=5, these changes bypass the workflows defined in your config files. Even when resources are managed using the Kubernetes provider, such updates can lead to mismatches between the desired and actual states. For example, scaling replicas for deployment or changing resource configurations through such methods may address an immediate need. However, these changes don’t update the state files, leaving them out of sync and no longer representing the current state of the cluster.
Automatic updates by controllers
Kubernetes controllers, like the ReplicaSet controller or Horizontal Pod Autoscaler (HPA), automatically adjust resource configurations to keep the cluster running. For example, if a pod crashes, the ReplicaSet controller will create a new pod to replace it. While these actions keep your applications available, they can lead to differences between the cluster’s state and what’s defined in your IaC configuration.
Outdated IaC Configurations
If changes are made directly in the cluster but not updated in the configuration files, the configurations no longer match. For example, if a service is changed from ClusterIP to LoadBalancer to provide external access, but the state file still defines it as ClusterIP, this creates a mismatch between the two. Over time, these differences make it harder to keep track of what’s running in the cluster.
Component issues
Issues within the cluster, such as a node becoming unhealthy or failing to operate, can lead to drift. For example, if a node goes down, Kubernetes shifts the workloads to other nodes, which may change how resources like CPU and memory are allocated. Similarly, a deployment with incorrect resource limits or outdated configurations might restart frequently or fail to run, forcing Kubernetes to adjust the environment. These changes, while necessary for keeping the cluster functional, create differences from the desired state defined in configurations.
Understanding these reasons is the first step toward preventing drift and keeping your Kubernetes cluster consistent and manageable.
How to Identify Drift in Terraform and Kubernetes
While knowing the causes of configuration drift helps you understand the problem, the next step is figuring out how to detect it. Terraform offers a method to identify drift by comparing the desired state defined in its configuration files and state file with the current state of the resources in the cluster.
The terraform plan command is at the core of this process. It creates an execution plan by analyzing the differences between what is defined in your configuration files and what actually exists in your cluster. Any mismatches are flagged as drift, giving you a clear understanding of the changes that have occurred within your cluster.
For example, if the number of replicas in a deployment is changed through a CLI command, running terraform plan will detect this and highlight the difference. Similarly, if a service type is altered from ClusterIP to LoadBalancer without updating the Terraform configuration, the command will show this difference.
This process not only helps identify drift but also outlines the necessary steps to fix it. After identifying the differences, running the terraform apply command can bring the resources back in line with the desired state. This makes sure that your cluster remains consistent and aligned with the configurations defined in your configuration files.
Detecting drift with Terraform is an important part of maintaining a stable Kubernetes cluster. It allows you to catch and resolve changes early, reducing the risk of misconfigurations affecting the overall environment.
Hands-On: Detecting Drift with Terraform Plan
After exploring how Terraform helps identify configuration drift, let’s now put it into a hands-on example. In this section, we’ll deploy Kubernetes resources using Terraform, introduce a drift by modifying the deployment outside Terraform’s workflow, and then use the terraform plan command to detect the drift. This example will show you how Terraform identifies changes and flags mismatches between the current state in the cluster and the desired state defined in its configuration.
We will deploy an Nginx deployment and a service in a Kubernetes cluster using Terraform. Initially, the deployment will be configured with two replicas, as defined in the Terraform configuration. Once the resources are deployed, we’ll intentionally modify the deployment by scaling it to five replicas using kubectl. This change introduces drift since Terraform is no longer managing the modified state. Using terraform plan, we’ll detect the difference, which will highlight the drift in the deployment’s replica count.
To start, let’s look at the Terraform configuration used for deploying the resources. The configuration starts with defining the required Kubernetes provider. This makes sure that Terraform can interact with your Kubernetes cluster to manage resources. The Kubernetes provider uses the kubeconfig file to connect to the specified cluster and manage resources efficiently.
The deployment resource defines an Nginx deployment with two replicas. Using the Kubernetes provider, we specify the desired state of the deployment, ensuring alignment with IaC definitions. The metadata section specifies the name of the deployment and assigns a label app: nginx for identifying the pods created by this deployment. The spec section describes the desired state of the deployment, including the number of replicas and the container configuration. The container uses the nginx:latest image and exposes port 80 for serving HTTP traffic.
The service resource defines a ClusterIP service to expose the nginx deployment within the cluster. The service uses the app: nginx label to select the pods created by the deployment. It forwards traffic from port 80 to the containers running within the pods.
To deploy these resources, run the following commands. First, initialize Terraform using terraform init to set up the Kubernetes provider.

After initialization, use terraform apply to create the resources in the cluster. The terraform apply command confirms that the deployment and service are successfully created based on the configuration.

Next, to introduce drift, we scale the deployment using the kubectl command:
This command changes the number of replicas in the Kubernetes cluster to five, but Terraform still defines the desired state as two replicas. This difference creates drift, as Terraform is unaware of the change.

Finally, we run the terraform plan command to detect the drift. Terraform compares the current state of the Kubernetes resources with the desired state defined in its configuration files. The output of terraform plan highlights the difference, showing that the number of replicas has been changed from two to five. This makes it easy to identify the drift and determine the exact changes made to the deployment.

This hands-on example shows how Terraform and Kubernetes together help detect configuration drift in clusters. By using terraform plan, you can identify changes that deviate from your desired state, giving you visibility into unauthorized modifications and helping you maintain consistency across your infrastructure.
How Can You Avoid Drift in Terraform and Kubernetes Clusters?
After understanding how to detect drift, the next focus should be on preventing it. Configuration drift can disrupt the stability and consistency of your Kubernetes clusters, making it harder to manage resources. To avoid these issues, adopting the following practices can help you minimize or completely eliminate drift:
Consistent use of IaC
Always define and manage your Kubernetes resources through Infrastructure as Code. Using tools like Terraform’s Kubernetes provider makes sure that resource configurations are centralized and consistently managed. Avoid making changes directly to the cluster using CLI commands or automation scripts, as these bypass IaC workflows and introduce inconsistencies. Using IaC makes sure that all changes are documented, version-controlled, and auditable, keeping the actual state aligned with the desired state.
Enforcing policies
Use policy engines like Kyverno to define and enforce rules within your Kubernetes cluster. These tools can restrict changes, such as scaling replicas beyond a limit or modifying service types, making sure that all updates comply with predefined standards set by the organization. This prevents changes made outside IaC workflows or without proper approval, reducing the risk of misconfigurations.
Regular audits
Perform scheduled audits using tools like kubectl or terraform plan to compare the current state of your Kubernetes resources with the desired state defined in your configuration files. These audits help you identify mismatches, such as changes in replica counts or service types, so you can resolve inconsistencies before they impact cluster stability.
Monitoring and alerts
Use monitoring tools such as Prometheus, Grafana, or Datadog to track changes in your Kubernetes cluster in real-time. Set up alerts to notify you of unexpected modifications, like changes in resource configurations or scaling. These tools help you quickly identify and address any kind of drift, making sure that your cluster remains consistent and predictable.
Now by combining these practices, you can create a strong strategy to prevent configuration drift within Kubernetes.
To follow these best practices for avoiding drift, you need multiple tools to monitor resource states, identify changes made outside IaC workflows, and make sure that resources match the desired configurations. Doing this manually can be a complex and time-consuming process, especially when working with large Kubernetes clusters. This is where Firefly comes in.
Using Firefly to Track and Resolve Drift in Kubernetes
Firefly provides a single platform to simplify managing drift in Kubernetes clusters. It gives you a clear view of all your resources and categorizes them as codified, unmanaged, or drifted.
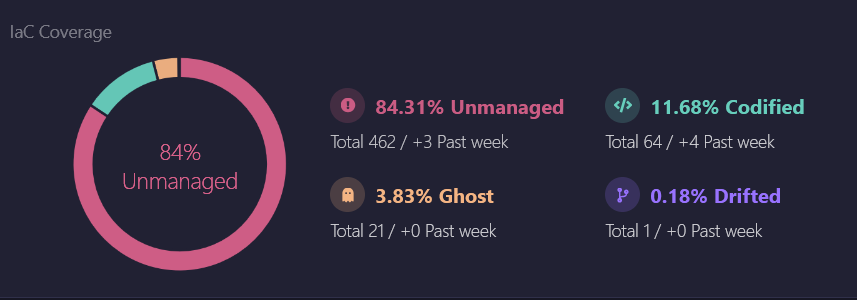
Firefly’s Dashboard makes it easy to identify drifted resources by highlighting them and showing detailed information about what has changed. For example, if a resource like deployment is modified outside Terraform, Firefly will flag it as drifted and display the differences between the current state and the IaC-defined state.
Additionally, Firefly provides a codified version of the drifted resources, allowing you to understand the exact changes made and helping you restore them to their desired state. This eliminates the need for manual comparisons, saving time and reducing complexity.

With Firefly, you can track all resources in one place, detect drift quickly, and maintain alignment between your Kubernetes cluster and your IaC configurations. It helps simplify the process of managing drift and keeps your infrastructure stable and predictable.
FAQs
Can Terraform fix drift in Kubernetes resources?
Yes, Terraform can fix drift in Kubernetes resources. When you run the terraform plan command, it detects drift by comparing the desired state defined in your configuration files with the current state of the resources in the cluster. After identifying the drift, you can run terraform apply, which updates the resources in the cluster to match the desired state specified in the IaC configuration.
What tools can help manage drift in Kubernetes clusters?
Tools like Terraform (using its Kubernetes provider) and policy engines like Kyverno or Open Policy Agent are commonly used to detect and manage drift. Terraform’s Kubernetes provider helps define and manage resources through IaC, while Firefly provides a detailed view of drifted resources.
Why is drift a common issue in Kubernetes clusters?
Drift often occurs in Kubernetes because of changes made outside IaC workflows, such as scaling deployments with kubectl, automated updates by controllers, or component failures like node crashes that force workloads to move unexpectedly.
How can you prevent drift in Kubernetes resources?
Drift can be minimized by consistently managing resources through IaC tools like Terraform, enforcing policies with tools like OPA or Kyverno, and regularly auditing cluster states to ensure they match IaC configurations. Monitoring and alerting systems also help detect unexpected changes in real-time.


