What is Terraform State?
Tracking infrastructure changes is crucial for maintaining consistency and avoiding errors. Without a reliable system to track changes, teams may lose sight of deployed resources, leading to mismatched configurations, failed deployments, or even accidental deletions. Terraform addresses this by using a state file, which acts as a detailed record of every resource in your infrastructure, including existing resources. This state file helps Terraform understand the current state of your resources and ensures that any planned changes are applied correctly, reducing the risk of errors and maintaining consistency across different environments.
The Terraform state file stores the configuration of your infrastructure, including resource details, metadata, and the current status of deployed resources. It acts as Terraform’s source of truth, enabling it to track resources and their configurations accurately.
When you run the terraform init command, it initializes the backend configuration, setting up the environment to store the state file in a remote location such as an S3 bucket. By using a Terraform backend like S3, teams can securely store the state file remotely, avoiding issues that come with using a local state file, such as potential data loss or conflicts in collaborative environments. The state file stored in the S3 bucket ensures that Terraform has access to the latest infrastructure data and can properly compare it against the desired configuration in the Terraform configuration files.
Without this state file, Terraform would not be able to track the resources that already exist, leading to inefficiencies, duplication of resources, or incorrect configurations. Proper management of the state file, whether through remote backends or careful handling of local state files, is essential for ensuring smooth, reliable, and consistent infrastructure management.
When using Terraform to manage infrastructure, improper handling of the state file can lead to critical issues like failed updates, misconfigurations, and resource conflicts. For example, if changes are made directly in the cloud console instead of through Terraform, it can cause a mismatch between the actual infrastructure and the state file, which is known as configuration drift.
Configuration drift can result in Terraform applying incorrect changes, accidentally modifying or deleting resources, and disrupting your infrastructure. Proper state file management is essential to avoid these risks and maintain consistent deployments.
When the Terraform state file is not properly managed, it can lead to deployment failures and security risks. For example, if multiple team members make simultaneous updates without locking the state file, it can result in conflicts or overwrites, causing mismatches in the infrastructure.
Moreover, Terraform state files often store sensitive information, such as resource IDs, secrets, or configuration data. If these files are stored in insecure locations or without encryption, unauthorized users can access this data, exposing your infrastructure to security threats. Proper state management practices, like using remote backends with encryption, enabling locking, and isolating environments with workspaces, are essential to avoid these issues.
Why State Management is Necessary in Terraform?
Mismanagement of Terraform state files can lead to serious issues. For example, without proper locking, simultaneous changes by team members can corrupt the state file, disrupting workflows. Sharing state files across environments without isolation can cause resources in one environment to overwrite another.
Collaboration Challenges in Teams
When team members work on the same resource without sharing the state file, their changes can clash. For example, running terraform apply at the same time can damage the state file, leading to incorrect resource updates or failed deployments.
Inconsistencies Between Environments
Using a single state file for multiple environments, like development and production, can cause resources in one environment to overwrite another. Additionally, if the state file isn’t updated correctly after changes, it can lead to mismatched infrastructure.
Security Risks
If you are not using a remote backend and state files are stored locally or without encryption, data like resource IDs, secrets, and metadata becomes exposed. This lack of security puts the data at risk, and accidental sharing or potential data breaches put your infrastructure at risk.
State management is important for avoiding conflicts, ensuring consistent infrastructure, and protecting sensitive data in Terraform workflows. You can create a secure and efficient workflow by implementing key practices such as using remote backends for centralized storage, enabling versioning to track changes, locking state files to prevent simultaneous updates, and isolating environments with workspaces.
Let’s explore how to implement these best practices in detail, focusing on practical steps and examples to ensure your Terraform state is managed effectively and your infrastructure remains stable and reliable.
Centralize State Management with Remote Backends
Storing Terraform state files locally presents several challenges. Managing state files on a local machine can be particularly problematic due to the lack of centralized control and the potential for conflicts. For example, without a shared backend, two team members running terraform apply at the same time can overwrite each other’s changes, corrupting the state file. If the local state file is deleted, Terraform loses track of resources, making recovery difficult. These issues can disrupt deployments and hinder team collaboration, leading to inconsistencies in infrastructure.
Using a remote backend for state management solves these problems by storing the state file in a secure, centralized location. For instance, with an S3 bucket as the backend, all team members can access the same Terraform state file, preventing conflicts. Consistency in infrastructure relies on secure state management, where features like encryption protect the data, versioning tracks changes over time, and state file locking prevents multiple operations from modifying the state file at once. This ensures that Terraform deployments are secure, consistent, and reliable.
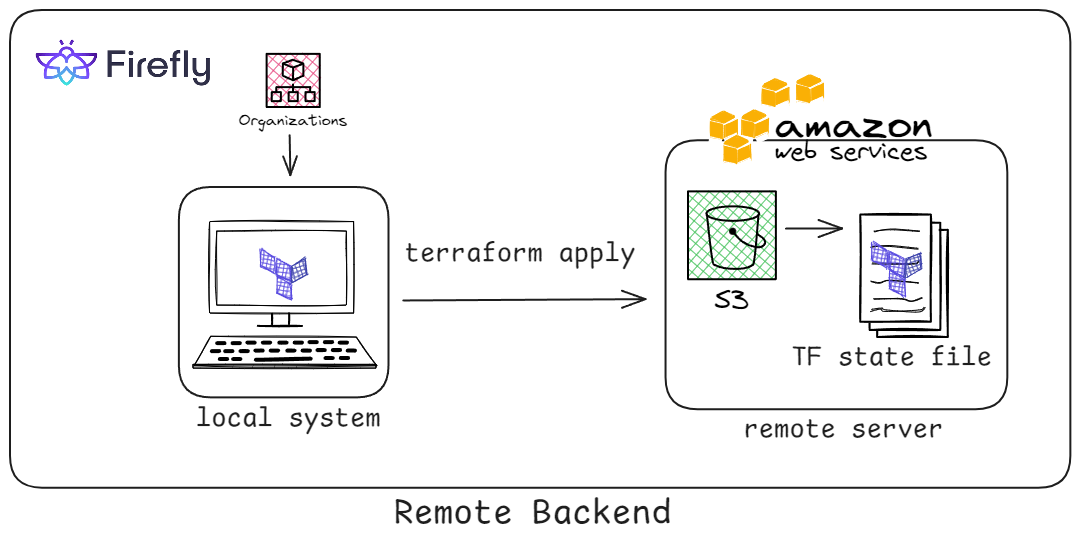
In this section, we’ll walk through configuring a remote backend with S3 to securely store Terraform state files, enable encryption, and ensure the state remains consistent and accessible for seamless team collaboration.
This Terraform configuration sets up an AWS EC2 instance while securely managing the state file using an S3 remote backend. The AWS provider is configured to use the us-east-1 region for creating resources. The backend block specifies an S3 bucket named terraform-state-mgmt-firefly to store the state file, with encryption enabled to protect sensitive data. The resource block defines an EC2 instance using the AMI ami-0e2c******6378d8c and an instance type of t2.micro, which is suitable for small workloads. Additionally, a custom tag, Name = “Terraform-state-mgmt,” is applied to label the instance for easy identification and management.
This setup securely stores the Terraform state file in an S3 backend, prevents conflicts by allowing centralized access for team collaboration, and ensures consistency in infrastructure deployments by tracking resource changes accurately.
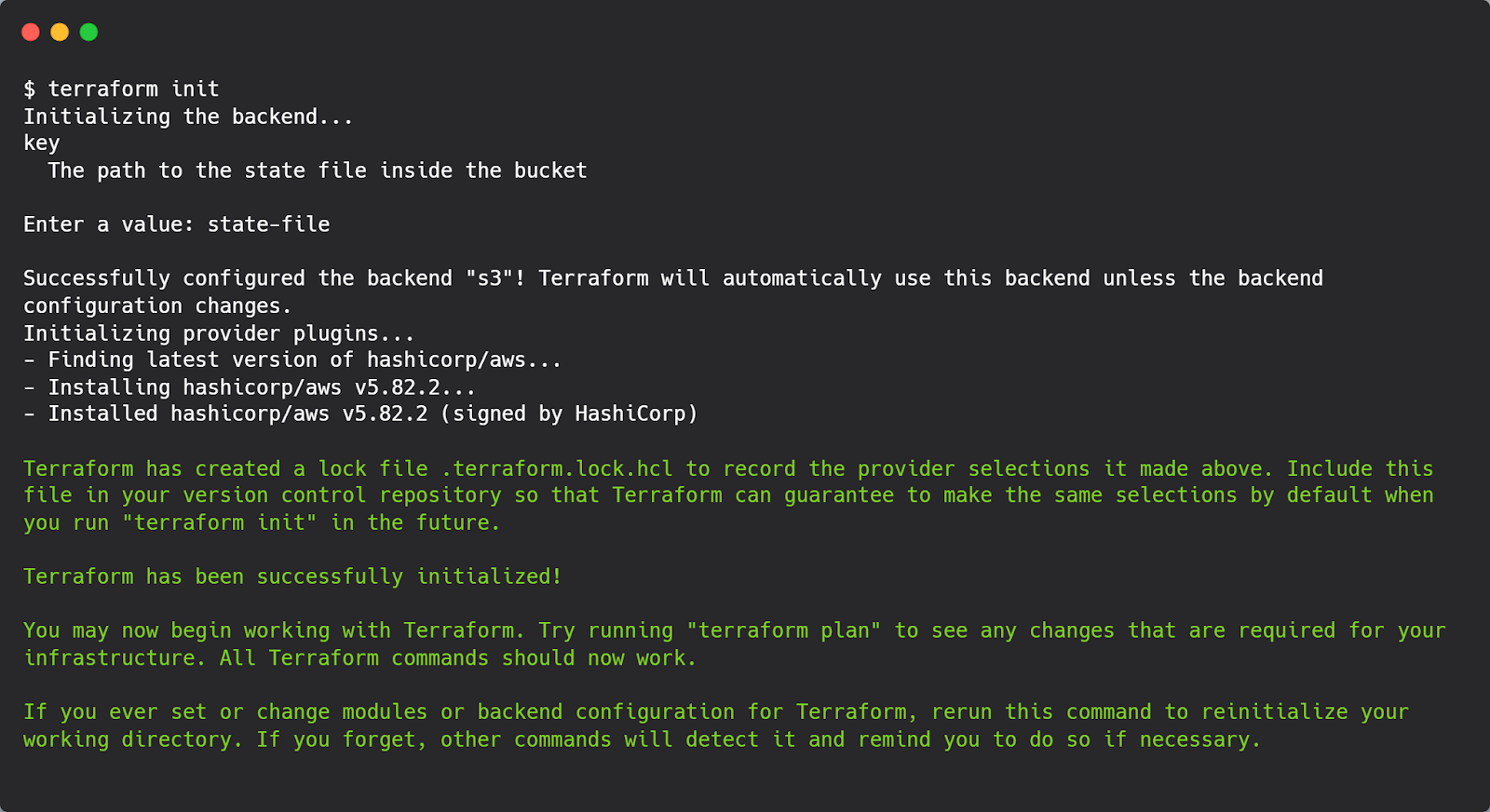
Moving further, by running the terraform command like: terraform init, we’ll have something like this :
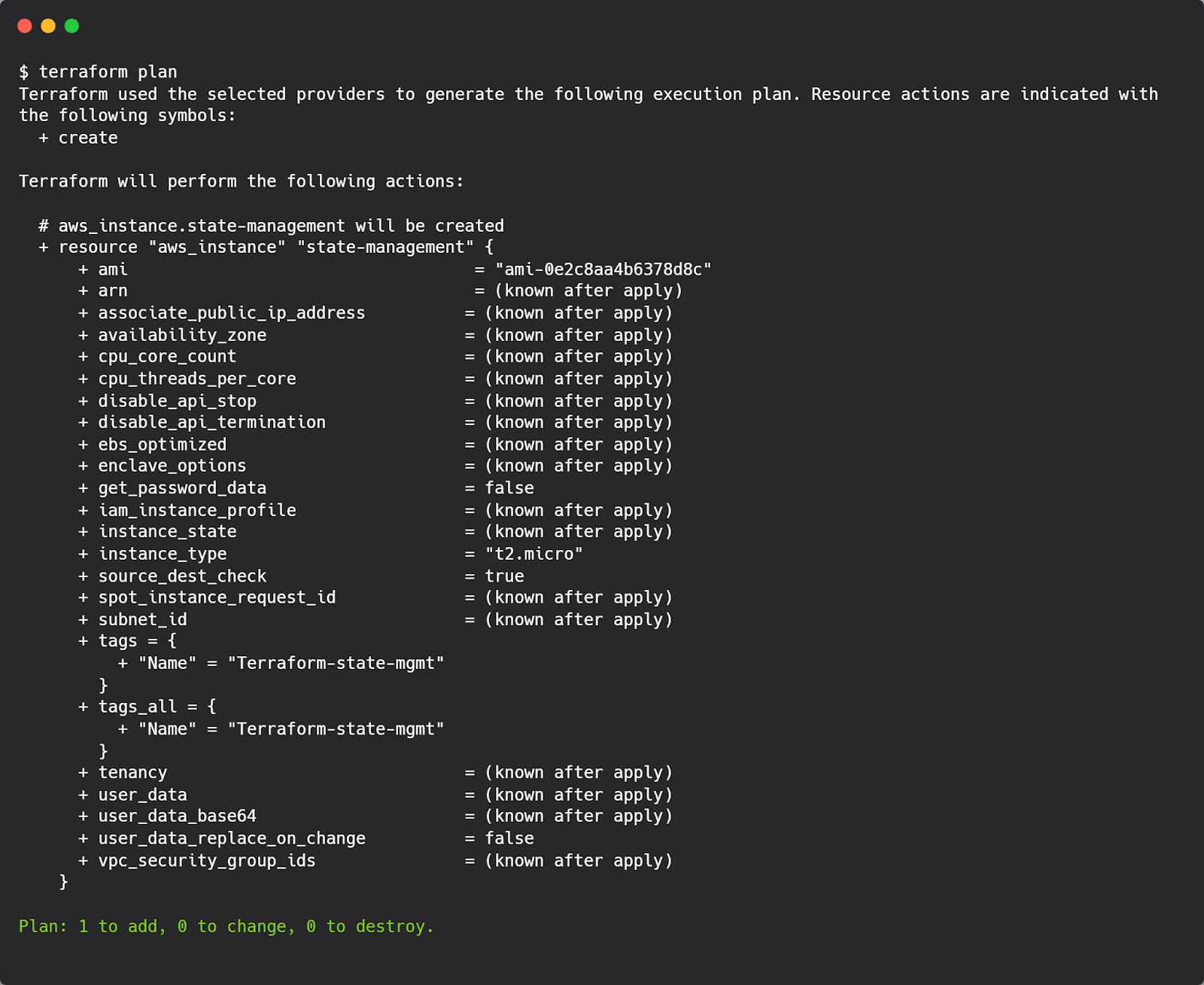
After executing terraform plan and terraform apply, we can expect results similar to this:
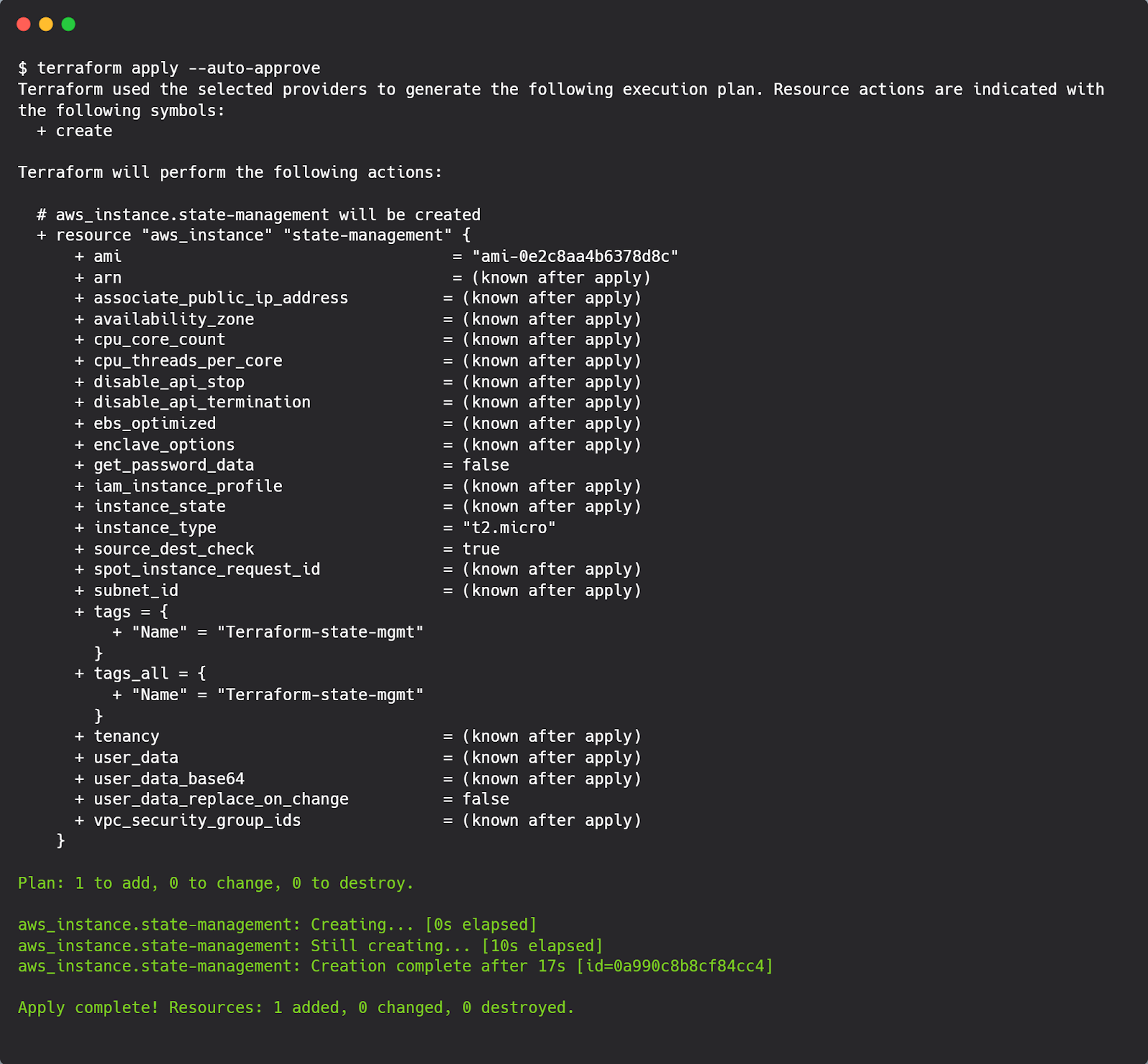
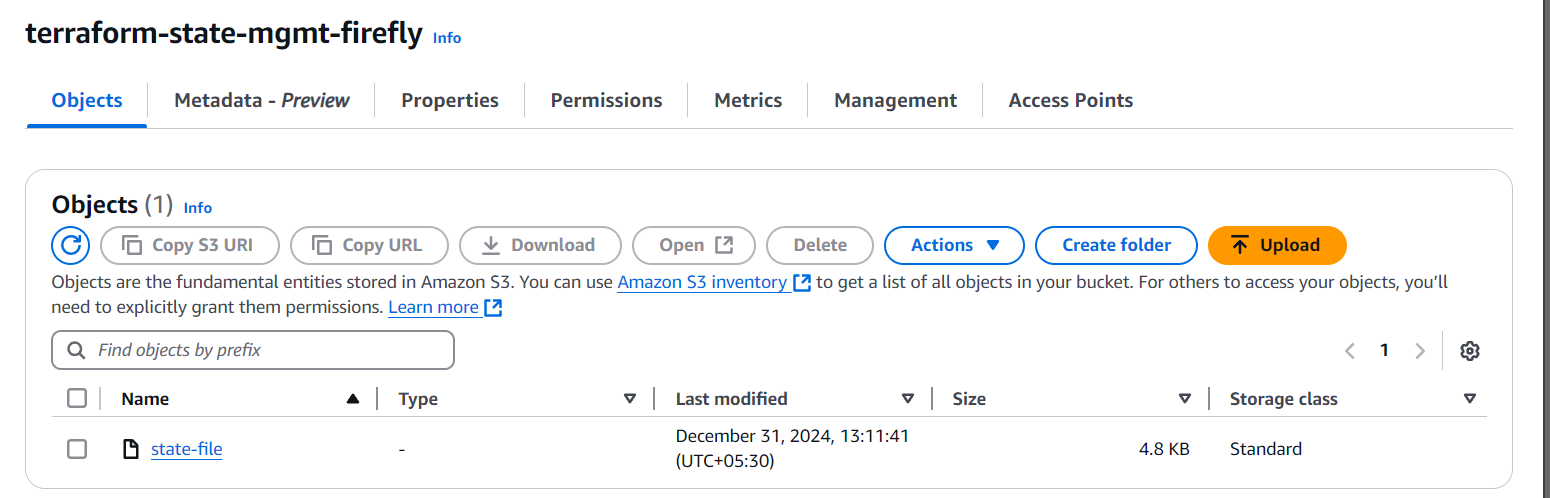
The image above shows the bucket named terraform-state-mgmt-firefly.
Remote backends play an important role in Terraform state management by providing a secure, centralized way to store and manage state files. They help prevent conflicts, make collaboration easier, and safeguard important data, enabling teams to manage infrastructure changes with reliability and confidence.
Track Changes with State File Versioning
State file versioning solves this issue by tracking all changes made to the Terraform state file. It lets you revert to previous versions if needed and helps you track how your infrastructure. Now, we’ll explain how versioning works and why it’s an essential practice for managing Terraform state files.
We’ll now guide you through enabling state file versioning using an AWS S3 bucket as an example. This process will help you track changes effectively, ensuring that your Terraform state remains secure and easily recoverable.
This Terraform configuration shows how to deploy an AWS EC2 instance and handle the state file using a versioned S3 remote backend enabled.
The AWS provider is configured to use the us-east-1 region for resource deployment. The backend block specifies an S3 bucket named terraform-state-mgmt-firefly to store the Terraform state file securely. Key configurations include enabling encryption (encrypt = true) to safeguard the state file and enabling versioning (versioning = true) to track changes over time, providing a way to recover in case of issues. The resource block defines an EC2 instance using the AMI ID ami-0e*******378d8c and sets the instance type to t2.micro, which is suitable for small-scale workloads.
We can enable the versioning by running the terraform init command followed by terraform plan and terraform apply.

Enabling state file versioning is an important step in strengthening the reliability and security of your Terraform workflows. By keeping a detailed record of every change made to the state file, versioning allows you to roll back to previous, stable states in case of errors. This practice enhances visibility into infrastructure changes, helps prevent mistakes, and ensures you can manage infrastructure updates with confidence as your environment evolves.
Locking State Files with Remote Backends
Managing Terraform state files in a team environment can lead to issues when multiple team members make changes simultaneously. For example, if two DevOps engineers run terraform apply at the same time, both operations may attempt to update the state file, leading to data corruption. This happens when one engineer’s changes overwrite the other’s, causing Terraform to lose track of the actual state of resources. As a result, the state file may become inconsistent or damaged, leading to deployment failures, mismatched resources, and incorrect updates. Without a proper locking mechanism in the backend, these issues can disrupt workflows, cause delays, and introduce inconsistencies in infrastructure, making it difficult to manage effectively. Additionally, using the state push command can help manage state file updates, although it is not the recommended best practice and should be used with caution.
State file locking addresses this problem by ensuring that only one operation can access and modify the state file at a time. This maintains the state file’s accuracy and reliability. By using remote backends like AWS S3 with DynamoDB, state locking is enforced, with DynamoDB ensuring that only one operation, such as terraform apply, can modify the state file at any given time. It locks the state file during critical operations, preventing conflicting changes and protecting the file from corruption. This ensures smooth, coordinated infrastructure updates and maintains consistency across the team.
State locking in Terraform helps prevent conflicts by ensuring only one operation modifies the state file at a time. This process is essential for maintaining consistent and reliable infrastructure management using Terraform backends like AWS S3 and DynamoDB.
Prevents Conflicts
State locking ensures that only one operation, like terraform apply, can modify the state file at a time. If two team members try to apply changes at the same time, one operation will pause until the other finishes. This prevents issues where both operations try to change the state file, which could corrupt it or cause resources to become mismatched. For example, one operation might overwrite the changes made by the other, causing Terraform to lose track of the current infrastructure.
It’s important to note that terraform plan does not lock the state file—it only generates a preview of changes and doesn’t modify the state. However, terraform apply locks to the state file during its operation to avoid these conflicts. Without locking, these issues can disrupt the deployment process, lead to inconsistent infrastructure, and require time-consuming manual fixes.
Enhances Workflow
In a team-based setting, where multiple people or automated systems are working on the same infrastructure, state locking plays a key role in preventing conflicts. For example, when a pipeline is applying changes to the infrastructure using terraform apply, state locking ensures that no one else can run terraform apply or make other changes to the state file at the same time. This prevents issues like overwriting each other's changes or corrupting the state file.
By locking the state file during operations, Terraform ensures that only one process can modify it at a time. This improves workflow efficiency by allowing the team or automation to focus on one change at a time, reducing the chances of errors and misconfigurations. State locking makes sure that updates are applied in the correct order, preventing conflicts and making collaboration more reliable and predictable.
Ensures Consistency
State locking makes sure changes to the state file are applied without any interruptions, keeping the infrastructure in sync with the Terraform code. For example, during terraform apply, it prevents incomplete or partial updates, ensuring all resources are created or updated correctly. This is important for maintaining stable infrastructure, especially when multiple people or automation systems are involved.
State locking protects the Terraform workflow by keeping the state file accurate and safe during important actions, reducing the risk of errors or conflicts.
To keep Terraform running smoothly and avoid conflicts, setting up state locking is crucial. Here’s how you can set up state locking using DynamoDB with an AWS S3 backend:
First, create a DynamoDB table that Terraform will use to manage locks. You can do this with the following AWS CLI command:
This AWS CLI command creates a DynamoDB table named terraform-state-lock for managing state locking in Terraform. Here's what each part does:
The --table-name terraform-state-lock command specifies the name of the DynamoDB table used to store lock information. The --attribute-definitions AttributeName=LockID, AttributeType=S part defines the primary attribute, LockID, which serves as the unique identifier for the lock, with AttributeType=S indicating it is a string. The --key-schema AttributeName=LockID, KeyType=HASH sets LockID as the primary key for the table, with KeyType=HASH meaning it will be used as the partition key. Lastly, the --provisioned-throughput ReadCapacityUnits=5,WriteCapacityUnits=5 allocates read and write capacity to the table, allowing it to handle up to 5 read and 5 write operations per second.
This command creates a table named terraform-state-lock with a primary key LockID of type string. The table’s read and write capacities are set to handle multiple requests efficiently.
Next, configure your Terraform backend to use the S3 bucket for storing the state file and DynamoDB for locking. Here’s an example configuration:
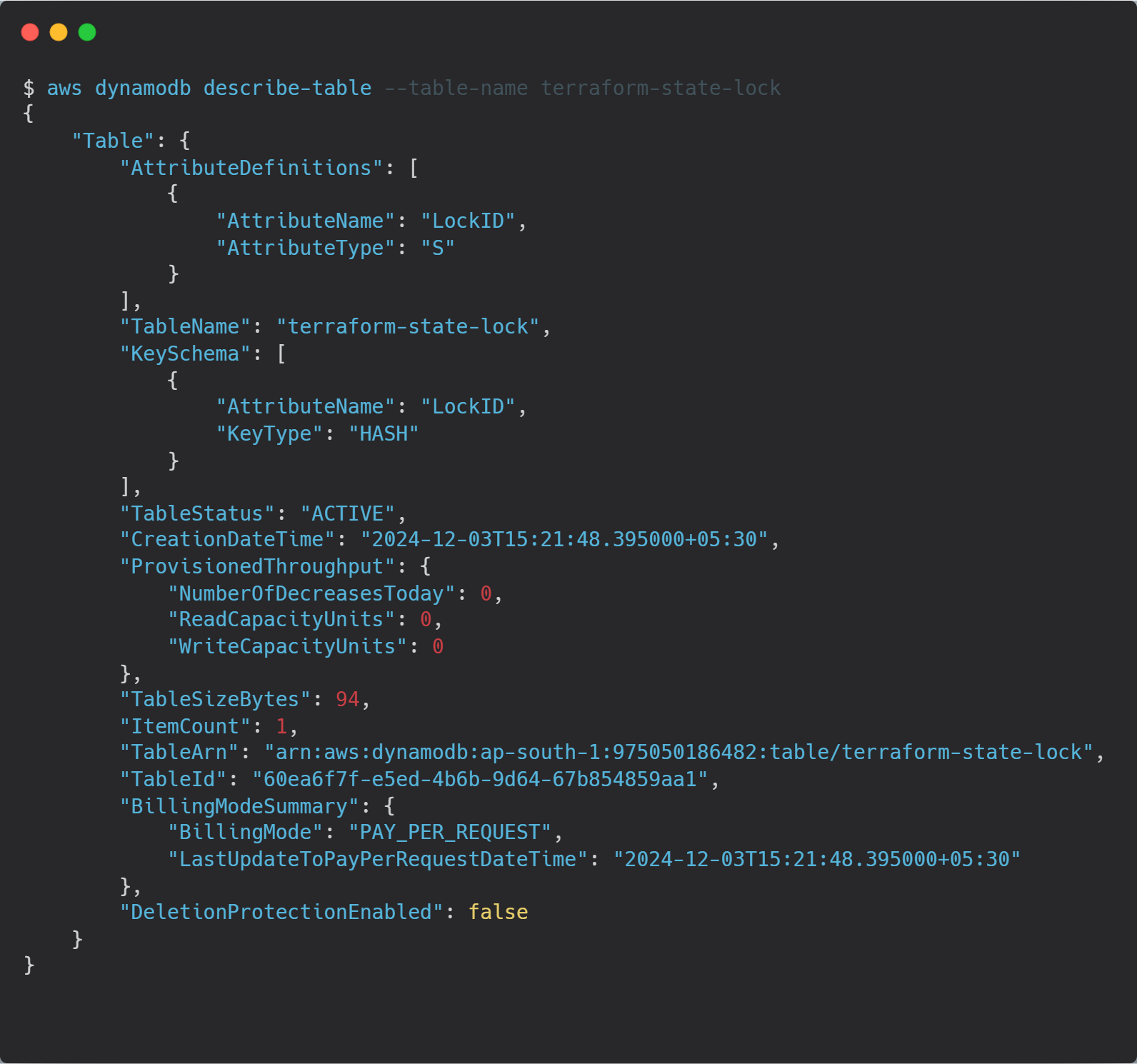
Using the aws dynamodb describe-table command, we can have the details of the dynamodb table.
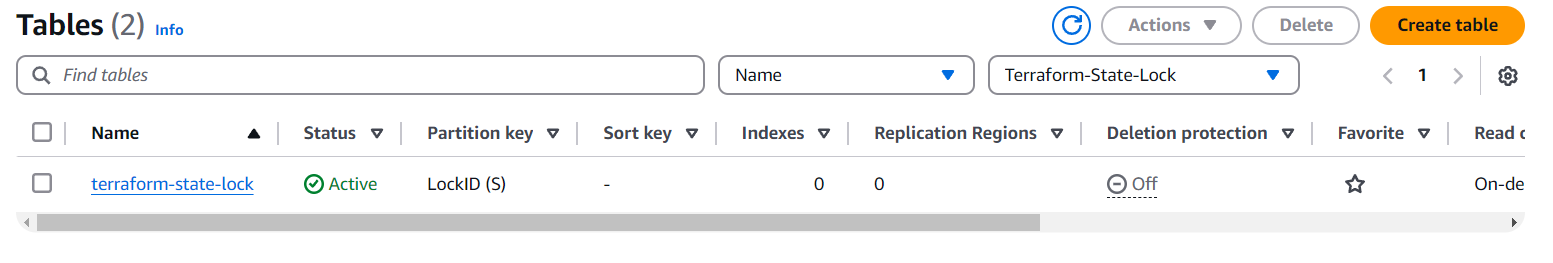
In the AWS Cloud Console, we can also access DynamoDB from the table.
Implementing state locking with DynamoDB helps keep your Terraform workflows smooth and free from conflicts. Ensuring that only one operation can modify the state file at a time prevents issues like overlapping changes, which could lead to errors or inconsistencies in your infrastructure. This practice protects the state file, reduces the risk of misconfigured resources, and ensures that infrastructure updates are applied consistently. It’s an essential step for teams working collaboratively on the same infrastructure.
Isolate Environments with Terraform Workspaces
Managing multiple environments like development, staging, and production can be difficult, especially when changes in one environment affect others. This can lead to issues such as overlapping configurations or updates being applied to the wrong environment.
Terraform workspaces help solve this by allowing each environment to have its own isolated state file while using the same configuration. Each workspace stores its own state, so changes made in one environment won’t impact others. This approach simplifies environment management and ensures changes are applied only where intended, reducing the risk of errors.
In this section, we’ll explain what Terraform workspaces are, how they work, and why they are essential for managing multiple environments effectively with a single configuration.
Workspaces simplify the management of environment-specific infrastructure by keeping each environment’s state and configuration separate. This makes tasks like testing changes in staging before applying them to production much easier, reducing the chance of errors and ensuring smoother, more reliable deployments.
Using Terraform workspaces is a simple but powerful way to handle multiple environments. In this section, we’ll show you how to create and switch between workspaces using commands like terraform workspace new and terraform workspace select. We’ll also demonstrate how workspaces help isolate state files, ensuring that each environment remains independent and free of conflicts.
These are the set of terraform workspace commands we can use :
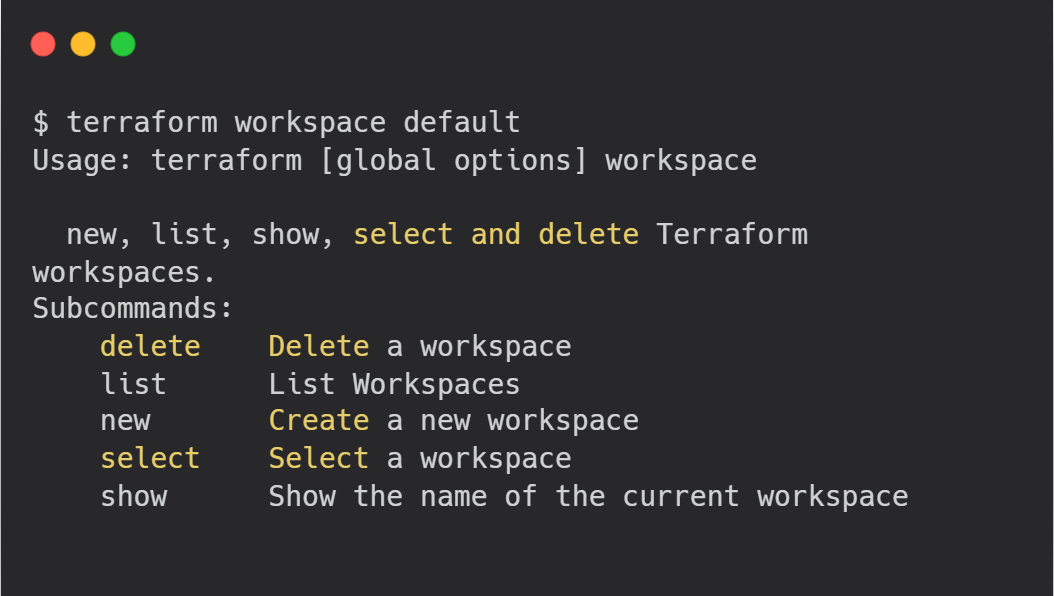
In the code above, you can use the terraform workspace show command to check the current workspace you are in. To create a new workspace, you can use the terraform workspace new <workspace-name>command, where <workspace-name> is the name you want to assign to the new workspace. This allows you to easily manage and switch between different environments in your Terraform configuration.
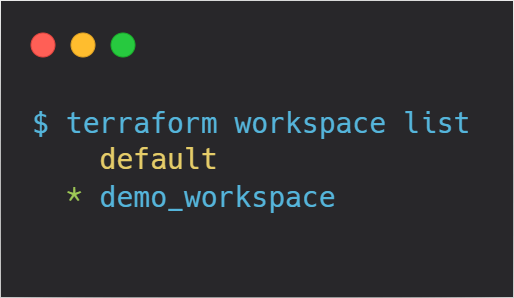
After creating a new workspace, running the terraform init command initializes the workspace. During this process, the workspace is registered, and a corresponding state file is created and stored in the specified backend (e.g., S3 bucket). This state file will be unique to the new workspace, allowing Terraform to track the resources and configurations separately for that environment.

In the env:/ folder, the workspaces are listed.


The image above shows that after creating a new workspace and running terraform init, the corresponding state file is stored in the backend (e.g., S3 bucket). This confirms that each workspace has its own isolated state file.
Using Terraform workspaces is an effective way to manage different environments, such as development, staging, and production, without mixing their configurations. Each workspace has its own state file, which prevents conflicts and accidental changes between environments. This approach ensures a more organized workflow, making it easier to deploy and maintain infrastructure across multiple environments.
Integrating Firefly
In this section, we’ll introduce Firefly and explain how it helps manage resources more effectively, with a particular focus on Terraform state backends. Firefly is a platform that enhances your Infrastructure as Code workflows by providing better visibility, automation, and efficient management of state files.
With Firefly, you can monitor the state file stored in your remote backend, such as AWS S3 or Azure Blob Storage, etc., and gain insights into the current infrastructure. It helps detect issues like configuration drift, unused resources, or inconsistencies between your Terraform code and the actual state. This allows teams to identify potential problems early and take corrective action before they impact deployments.
Firefly is built to work alongside Terraform, offering better visibility, automation, and management of your infrastructure. It aligns with best practices for state management, helping ensure your environments remain secure, consistent, and reliable.
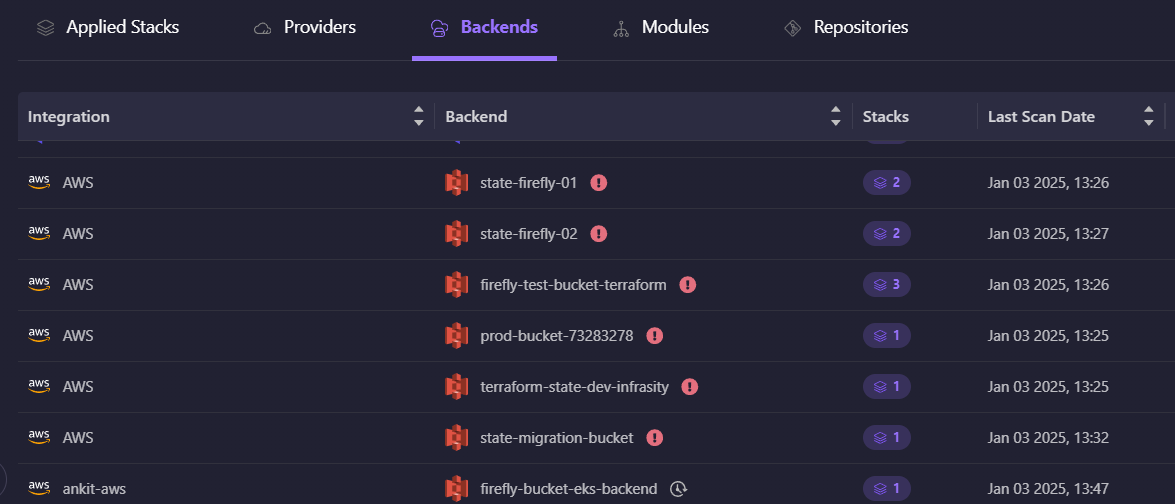
Monitoring Remote Backends
Firefly integrates with remote backends like AWS S3 and Azure Blob Storage to monitor state files. It ensures that state files are securely stored, tracks changes over time and detects any issues like inconsistencies or mismanagement. By continuously monitoring the state backend, Firefly helps keep your Terraform state file reliable and accessible. You can also view all connected backends in one place.
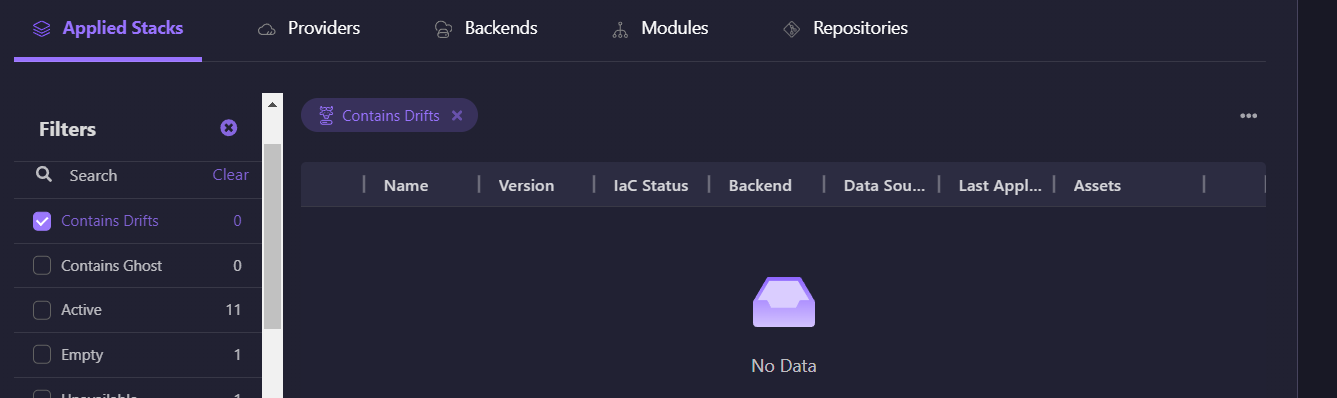
Detecting Configuration Drift
One of Firefly’s key features is its ability to detect configuration drift. This happens when the actual state of resources differs from the state file, often due to manual changes made outside of Terraform. Firefly regularly checks for these differences, alerts you when drift is found, and gives you clear suggestions on how to bring the resources back in line with the Terraform configuration. You can see all the resources affected by drift in one place.
Supporting Versioning and Locking
Firefly works with versioning and locking in remote backends to improve state management. By tracking state file versions, teams can review past changes and roll back if necessary. It also enforces state file locking, preventing multiple operations from modifying the state at the same time and ensuring consistent deployments.
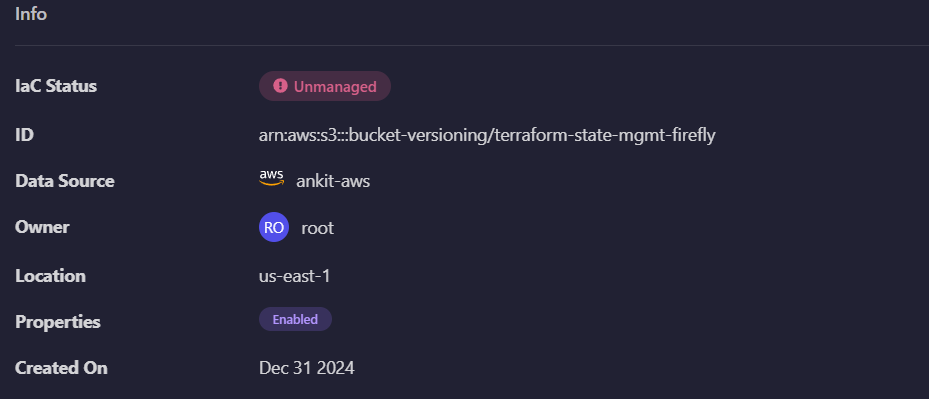
Firefly helps identify resources by categorizing them as either unmanaged or codified. Codified resources are those defined and managed through Infrastructure as Code, while unmanaged resources are not tracked in your code. This classification makes it easier to understand and organize your resources, ensuring nothing is overlooked or left out of your Terraform workflows.
Simplifying Environment Management with Workspaces
Firefly makes managing multiple environments, like development, staging, and production, more efficient. It provides insights into each workspace’s state, helping you monitor resource usage, identify unused resources, and maintain isolation between environments. This ensures that changes in one environment do not unintentionally affect others.
Enhancing Security
State files often contain sensitive information, such as resource metadata or outputs. Firefly strengthens security by integrating with Terraform’s encryption and access control features, ensuring that sensitive data in the state file remains protected. It also flags potential vulnerabilities, such as publicly accessible resources, helping teams address security gaps proactively.
FAQ
What is state management in IaC?
State management in Infrastructure as Code (IaC) involves tracking the current state of resources to ensure that infrastructure matches the desired configuration defined in the code. In Terraform, this is handled through a state file, which records resource information and helps identify changes to apply.
Where is the best place to store Terraform state files?
The best place to store Terraform state files is in a remote backend, such as AWS S3, Azure Blob Storage, or Terraform Cloud. These options provide secure, centralized access, enable encryption, and support features like versioning and locking to prevent conflicts and ensure reliability.
When to use state management?
To manage Terraform state effectively, use remote backends for secure storage, enable versioning for tracking changes, implement state locking to avoid conflicts, utilize workspaces to isolate environments, and regularly clean up unused resources to keep the state file accurate.
How do you manage state management?
To manage Terraform state effectively, use remote backends for secure storage, enable versioning for tracking changes, implement state locking to avoid conflicts, utilize workspaces to isolate environments, and regularly clean up unused resources to keep the state file accurate.


