Let us say that you are working with an organization that is managing its cloud resources across development, staging, and production environments. In the staging environment, a storage bucket configured for testing allows public access, which can easily expose internal logs or user data to the internet. In production, a database that stores customer information lacks encryption, which may lead to non-compliance with regulations like GDPR. In the development environment, some instances have inconsistent or missing tags, making it difficult to manage dependencies or identify which team owns specific resources during troubleshooting.
In this blog, we’ll explore how Terraform modules can simplify cloud governance for your infrastructure. We’ll cover the basics of cloud governance, discuss the importance of governance policies, and show how Terraform modules help enforce these policies with some hands-on examples.
What is Meant by Cloud Governance?
Cloud governance is the process of creating and enforcing policies to manage your cloud resources in a more secure, organized, and cost-effective way. It makes sure that every resource within your cloud, like storage buckets, databases, or instances, follows specific policies for security, access, and usage. For example, cloud governance for your organization might require that all databases storing customer data should have encryption enabled or that storage buckets used for backups have proper access controls to prevent unauthorized access. It can also include limiting resource usage to control costs and requiring consistent tagging across resources to track their ownership and purpose.
Without proper governance, resources might be deployed in regions far from their intended users, such as running an EU-based application in the Asia Pacific region. This is problematic because it increases latency for users and can violate data residency laws like GDPR, which require certain data to remain within specific geographic regions. Over-provisioned instances, such as using high-performance computing like m5.4xlarge for a simple application with low traffic, result in unnecessary costs for the organizations. Poor scaling configurations can lead to critical applications crashing during high traffic or resources being underused during quieter periods. Governance makes sure that resources are deployed in the right regions, configured efficiently, and appropriately scaled to prevent these kinds of issues.
By setting clear governance rules, organizations can prevent issues like running workloads in regions with high latency, using oversized instances for basic tasks, or forgetting to shut down environments after projects end. It helps DevOps teams apply consistent security configurations, manage costs effectively, and meet compliance requirements. Cloud governance ensures that your cloud resources are used efficiently and stay aligned with business goals.
What are Cloud Governance Policies?
Cloud governance starts with specific policies that define how resources are managed within your infrastructure. These policies set clear rules for creating, organizing, and configuring resources to make sure that they are secure, efficient, and meet compliance requirements for their organization. Let’s take a look at some of the key policies in detail:
- Tagging Standards: Tags are important for organizing and tracking resources effectively. For example, adding a tag like Environment: Development or Environment: Production helps identify which environment a resource belongs to. Similarly, a tag like Owner: Admin Team makes it clear who is responsible for managing that resource. This level of detail makes sure that resources are not only easy to locate but also properly accounted for. A good tagging policy helps DevOps teams identify the resources that are no longer needed or improperly configured. For example, a testing server deployed in production that was supposed to be temporary but was never shut down. Without a proper Environment tag or Owner tag, it might go unnoticed, running for months and adding unnecessary costs to the organization’s pocket.
- Resource Quotas: To prevent any overuse of resources and any unnecessary costs, organizations set resource quotas as part of their cloud governance policies. For example, limiting the number of instances in a testing environment makes sure that only the required resources are deployed. Similarly, setting quotas for storage can prevent large amounts of unused data from occupying infrastructure space and driving up costs. These quotas help DevOps teams avoid resource sprawl and ensure efficient usage within the organization’s budget.
- Network Configuration: Network configuration rules keep your cloud secure and well-organized. For example, assigning CIDR ranges like 10.0.1.0/24 for the production environment and 10.0.2.0/24 for development makes sure that the traffic stays separate between these two environments. Firewall rules, like allowing access only from specific IP addresses, limit who can connect to resources like instances or databases. For example, only trusted office networks or VPNs can access these resources, blocking unknown sources from viewing the data or making any changes. These rules make sure only approved users can use your resources, reducing the risk of data leaks or any mistakes.
- Identity and Access Management (IAM): IAM policies control who can access which resources in your cloud. For example, restricting access to databases so that only the database admin team can make changes and make sure that all the customer information is protected. Another example is creating temporary access for freelancers or interns working on a specific project, with permissions automatically revoked once the project is complete. These policies help protect important resources while allowing teams to perform their tasks more efficiently.
- Cost Controls: Cost controls help organizations manage their cloud expenses by setting some clear rules. For example, blocking the use of GPU instances like p4d.24xlarge in development environments avoids spending on high-performance computing that isn’t needed at all. Similarly, restricting deployments to cost-effective regions like us-east-1 instead of ap-northeast-1 helps reduce a lot of unnecessary costs. These policies ensure that resources are used efficiently and that cloud spending stays within the organization’s budget.
- Security Compliance: Security compliance policies help your cloud follow security rules and legal requirements. For example, enabling encryption on databases that store customer details protects information from being exposed to the internet. Setting up access logs for S3 buckets allows you to track who accessed specific files, which helps in audits and meeting regulations like GDPR. These policies keep your data safe and ensure your cloud is prepared for compliance checks as well.
These policies help many organizations manage their cloud resources in a more structured way, reducing risks and making sure that everything runs efficiently and securely.
What is a Terraform Module?
Cloud governance relies more on keeping resources consistent, secure, and also easy to manage across all the existing environments within your infrastructure. Without a clear approach, defining resources like instances or networks for each environment can lead to some repeated work for the DevOps engineer. Terraform modules help solve this problem by letting you reuse configurations to enforce the same rules everywhere.
A Terraform module is a group of Terraform configuration files that define specific resources. You can think of a module as similar to a function in programming, like in C++ or Java. A function takes input values and performs a task, then gives an output. In the same way, a Terraform module takes inputs, creates resources like subnets or databases, and provides outputs such as resource IDs or IP addresses. This saves a lot of time and ensures consistency between different environments, such as development, staging, and production, by avoiding the need to rewrite the same code for each environment.
Here’s how a Terraform module is structured:
- Inputs – These are variables you pass to the module to customize it, like specifying a region or subnet CIDR block for a specific environment.
- Resources – These are the actual resources the module creates, such as storage buckets, servers, or databases.
- Outputs – These provide useful details about the resources, like an IP address or a database connection string, that can be used in other parts of your setup.
Now, to use a Terraform module, you simply call it within your configuration by specifying the module source and any necessary inputs. Here’s an example:
In this example, the module located at ./modules/firefly_module is called, and inputs like region, firefly_bucket, and tags are passed to customize the setup.
Using Terraform modules makes it easier to follow governance policies by keeping your infrastructure consistent, secure, and manageable across all environments.
What is the Use of Terraform Module?
Now, let’s take a look at some of the use cases where modules simplify your infrastructure management:
- Multi-Environment Deployments: Firstly, the most commonly used case for Terraform modules is deploying the same infrastructure across multiple environments, such as development, staging, and production. For example, a module for creating a VPC can be reused with different inputs like CIDR blocks or instance types, making sure that all the environments follow the same structure and setup for their TF configuration.
- Networking Configuration: Managing networks becomes much easier with Terraform modules. For example, you can create a module that defines subnets, route tables, and NAT gateways for a VPC. This module can be reused to deploy networks in different environments, such as staging or production while keeping configurations consistent throughout all the environments. It makes sure that public subnets route traffic through an Internet Gateway and private subnets use a NAT Gateway for secure Internet access. By regularizing these setups, modules simply reduce the chances of any misconfigurations.
- Container Orchestration: Another important use case for Terraform modules is managing containerized environments. For example, setting up an EKS cluster involves configuring several components, such as node groups, IAM roles, and security groups. Now, by using a Terraform module, you can easily define these configurations once and reuse them across environments like development and production. This makes sure that each cluster has the same node scaling policies, secure role-based access, and proper network configurations. By reusing the module, you avoid errors and maintain consistency without needing to recreate the setup for every environment.
- Compliance Automation: Lastly, Terraform modules are highly effective for enforcing compliance requirements across your infrastructure. For example, a module designed for creating S3 buckets can automatically enable server-side encryption, set up logging to monitor access and all the activities, and block public access to make sure that no unauthorized user can view or modify the data in that bucket. By using a module, every S3 bucket you create will follow the same compliance standards, such as GDPR or SOC 2, without requiring any additional configuration. This simplifies meeting regulatory requirements and ensures that no important compliance steps are missed.
Using Terraform modules for these tasks enforces consistent configurations and automates compliance with governance policies across all the environments.
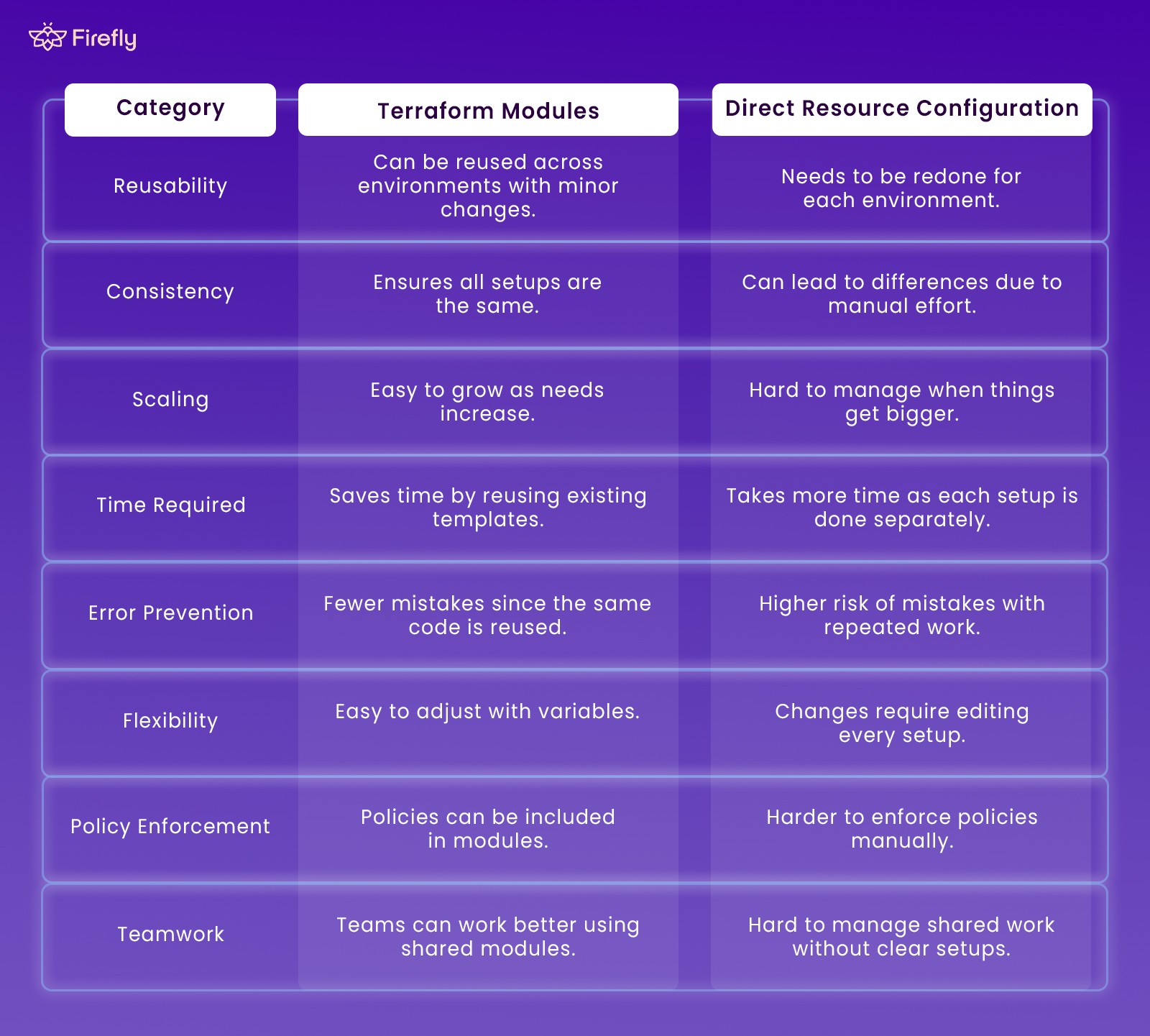
Terraform Modules vs Direct Resource Configuration
Now, what happens if you’re not using modules? Without them, direct resource configuration becomes the norm, where every environment requires writing resource configurations from scratch. This approach increases the risk of inconsistencies between environments and a lot of time being wasted.
The table below highlights the key differences between Terraform modules and direct resource configuration:
How do Terraform Modules and Cloud Governance Works Together?
After comparing Terraform modules with direct configuration, it’s clear that modules make your infrastructure management much simpler. But how do they align with cloud governance? The answer lies in the module’s ability to standardize and enforce governance policies through consistent configurations.
Terraform modules bridge the gap between governance rules and their implementation within your infrastructure. For example, a module for S3 buckets can enforce encryption, access controls, and logging by default, making sure that all buckets comply with security and compliance requirements. Similarly, modules for IAM roles or networking can define consistent policies for access control and traffic segmentation.
With a single module, you can deploy resources that follow the same tagging standards, scaling configurations, and cost controls, making sure that governance is applied everywhere. As your infrastructure scales, scaling governance policies becomes much easier with modules. Instead of redefining rules for every new resource or environment, you can reuse modules to make sure that the same policies are enforced.
By combining Terraform modules with cloud governance, organizations can manage resources more effectively, enforce security and compliance, and scale without losing any control over infrastructure standards.
Building Reusable Terraform Modules for Cloud Governance
Now that we’ve seen how Terraform modules align with cloud governance, let’s put this into practice. In this section, we’ll create a Terraform module to enforce governance policies for S3 buckets. This module will handle some important configurations like versioning, encryption, and public access blocking, making sure that every S3 bucket complies with governance standards.
The goal here is to simplify bucket management for multiple environments by requiring only the bucket name to be defined. All other configurations will be handled within the module.
Now, the module should be created in the modules/firefly-s3-bucket directory and will include the following Terraform resources:
1) S3 Bucket Creation: The aws_s3_bucket resource provisions the S3 bucket and assigns tags for identification.
2) Bucket Versioning: The aws_s3_bucket_versioning resource enables or disables versioning based on input variables.
3) Server-Side Encryption: The aws_s3_bucket_server_side_encryption_configuration resource makes sure that all objects in the bucket are encrypted using the specified algorithm.
4) Public Access Blocking: The aws_s3_bucket_public_access_block resource blocks all public access to the bucket.
The module accepts several variables to make it reusable across environments. These variables are defined in the module’s variables.tf file:
Once the module is set up, it can be used in the environment configuration, such as env/dev. The firefly-s3-bucket module is called with specific inputs that are specific to the development environment:
Variables for the environment configuration are defined in env/dev/variables.tf:
To deploy the S3 bucket with governance policies enforced, initialize the environment configuration by running terraform init in the env/dev directory.

Then, preview the changes by running the terraform plan command in the env/dev directory:

This will generate an execution plan, showing the resources that will be created, updated, or destroyed. Review the output carefully to make sure that the changes align with your expectations.
Once you are done with the plan, apply the changes to create the resources using terraform apply command.

After applying, the S3 bucket is created in AWS with all governance policies enforced. This makes sure that versioning is enabled or disabled as required, server-side encryption is applied, and public access is fully restricted. By reusing the module across environments, governance policies are consistently enforced without any repeated configuration effort.
Now, setting up governance using Terraform modules is a great way to ensure consistency, security, and compliance within your infrastructure. However, it can be a long and complex process as well. Creating and managing modules for every policy takes time, especially as your infrastructure scales.
Firefly’s Cloud Governance
This is where Firefly makes things easier. Instead of building everything from scratch, Firefly provides built-in policies ready to use. These policies save time and effort by automatically applying governance rules to all the resources within your infrastructure. You can also create custom policies to match your organization’s specific needs.
With Firefly, you can easily detect misconfigurations, track violations, and ensure compliance across all environments. Whether it’s securing S3 buckets, managing IAM permissions, or setting up network rules, Firefly gives you a clear view of your cloud’s governance. It simplifies the process and helps you maintain control without the extra workload.
Let’s take a closer look at how Firefly’s built-in policies and tools make governance easier.
Firefly makes cloud governance much simpler just by organizing policies into easy-to-understand categories. For example, you can focus on Access Control, Insecure Configurations, or Networking and Firewall rules. These categories help you quickly identify areas that need attention and fix issues efficiently.

Firefly also supports important frameworks like PCI DSS, SOC 2, and HIPAA. These frameworks make sure that your cloud setup meets industry standards as well without requiring any extra work from your end.

Additionally, Firefly includes policies for areas like Cloud Waste and Tagging, making it easier to manage costs and resource organization.
With these built-in features, Firefly helps you enforce rules across your infrastructure automatically. It shows exactly where you need to improve security or fix any problems, saving you a lot of time while keeping your cloud secure and well-organized.
FAQs
What are AWS Terraform modules?
Terraform modules are reusable folders of Terraform code that provision infrastructure. An AWS module contains resources from the AWS provider; for example, VPC, EC2, IAM, or S3. Modules help avoid repeating the same Terraform code across environments like dev, staging, and prod.
What are the types of modules in Terraform?
Terraform has two main types of modules:
- Root module: the directory where you run
terraform apply. - Child module: reusable module called from the root module or another module.
Modules can be stored locally or published to a registry for reuse.
How to create multiple EC2 instances using a Terraform module?
Inside the module, use the count or for_each meta-argument on the aws_instance resource. Then pass a variable like instance_count = 3 from the root module. Terraform loops based on that number and creates multiple EC2 instances from the same module.
How do I publish a Terraform module to the private registry?
Push the module to a Git repo and tag a release (example: v1.0.0). In Terraform Cloud/Enterprise, go to the Registry section and import the repo. After that, teams can reference the module using source = "app.terraform.io/org/module/aws".


