Today, 72% of organizations are moving towards using cloud-based services and Software as a Service (SaaS) platforms — and in turn, seeing more flexibility, cost savings, and continuous improvements for their business. But unfortunately, nearly all of them face challenges in keeping their infrastructure secure.
Typically, a Chief Information Security Officer (CISO) is responsible for preventing any data breach and identity loss by ensuring that security policies and governance are in place, and that continuous threat monitoring is performed as the infrastructure continuously expands.
Yet as more cloud services and applications are added to the infrastructure, maintaining control over those services becomes more and more difficult. For CISOs, infrastructure-as-code is the solution that solves their most complicated infrastructure security issues.
But in the modern cloud era, it's no longer enough to simply implement Infrastructure-as-Code (IaC) solutions. Optimizing for full coverage is essential for scalability, compliance, and overall cloud efficiency.
Here’s why (and how you can achieve 100% IaC coverage).
How Every CISO Can Benefit from IaC
Infrastructure-as-Code (IaC) offers practitioners a way to manage cloud resources by using code instead of doing everything manually using the cloud’s console, CLI, or scripts.
For a CISO, IaC offers a more efficient way to manage cloud resources, whether they reside in a data center or the cloud, by making sure that every resource or service within the cloud follows security policies consistently with the best practices in place. IaC allows you to see exactly how each resource, like a server or a database, is configured, so you can make sure it’s always created with the right security settings in place. Plus, it reduces the chance of errors or incidents, such as sensitive data breaches or exposing applications, since IaC allows you to use reusable pieces of code and see your changes in the plan before they are deployed to the cloud.
Let’s look at how it helps in maintaining a secure and well-managed cloud environment:
- Consistency and Reusability: With IaC, such as Terraform or OpenTofu, you can make use of reusable components, loops, or functions. These help deploy the same resources or configurations without repeating the code and maintain consistency in the infrastructure. For example, if you need to deploy multiple AWS EC2 instances, Terraform loops help you deploy the same security group settings, firewall rules, and configurations, reducing errors or mismatched configurations.
- Integration with CI/CD pipelines: When using IaC with CI/CD tools like GitHub Actions, it ensures continuous deployment of the resources rather than a big bang deployment, which might cause failures and longer downtime. For example, a developer can raise a PR for a new feature that is reviewed and merged, which triggers the Terraform deployment updating Amazon Web Services resources like an RDS database or an ELB load balancer. These continuous deployments ensure that everything is configured correctly and securely without any manual steps from anyone.
- Quick environment replication: IaC allows you to test your infrastructure before deploying it to production to ensure that a secure and protected infrastructure is deployed. For example, using Terraform workspace, you can easily create a completely separate testing environment workspace with the same configuration as your production setup. This way, you can safely test and make sure security policies work as expected before applying changes to your main environment.
Why IaC Coverage Matters for Infrastructure Security
Now that we’ve seen the common infrastructure security issues, let's take a look at how IaC can help in fixing them.
Preventing Misconfigurations
By using IaC, you can ensure that both hybrid cloud and cloud-native resources are always set up correctly according to your security policies, which simply reduces the risk of mistakes. Let’s say you are deploying an AWS S3 bucket using Terraform, so you can define in the Terraform code that public access should be turned off for this bucket and blocked. This IaC setup prevents accidental exposure of sensitive data and makes sure that all S3 buckets follow the organization's security standards without any extra effort. You can also review the configuration in your Terraform plan.
Securing Open Ports
With IaC, you can define and control which ports should open or close to access your cloud resources, ensuring that only necessary access is allowed. For example, in an AWS EC2 instance, your Terraform code config allows port 22 (SSH) access from a specific IP range, such as your office network. This means that even if someone tries to access the instance from outside this range, they won’t be able to connect to it. Additionally, having secure configurations in place makes disaster recovery more efficient, as all restored resources will maintain the same security policies, reducing risks during the recovery process. This simply reduces the risk of unauthorized access and keeps your infrastructure more secure by strictly controlling who can reach or connect to your cloud resources.
Enforcing Encryption
With IaC, you can make sure encryption is applied to your cloud resources by specifying it in your code. For example, when creating an AWS RDS database with Terraform, you can define encryption settings in the configuration. This way, whenever the database is deployed, all data will be encrypted by default. This reduces the chance of manual mistakes and helps protect your sensitive data. However, it's important to remember that encryption is only applied if it's included in the IaC configuration of your resources, so adding it is a key step in keeping your infrastructure secure.
Ensuring Consistent Compliance
IaC makes it much easier to maintain compliance with industry regulations, security policies, and best practices for authentication and authorization by enforcing different types of access control, such as Role-Based Access Control (RBAC) or Attribute-Based Access Control (ABAC). For example, if your organization needs to follow specific data privacy or Identity and Access Management (IAM) rules, you can define these compliance requirements directly in your Terraform code. When creating an AWS EC2 instance or S3 bucket, the IaC configuration ensures that proper access control models, such as Role-Based or Attribute-Based Access Control, are applied to meet security standards, such as enabling encryption or restricting public access. This way, every cloud resource is set up correctly from the start, which helps you avoid costly compliance violations and keep your infrastructure aligned with security best practices.
Exploring Tactical Real-World Examples (And Step-by- Step Instructions)
Now, let's dive into some real-world scenarios to understand how IaC tools, such as Terraform or OpenTofu, can help you with infrastructure security issues. We’ll be using Terraform throughout these examples to set up and manage the AWS resources.
Preventing Misconfigurations with S3 Buckets
When setting up an AWS S3 bucket through the AWS console or CLI, there’s a risk of misconfiguring the S3 bucket to be publicly accessible or inconsistent configuration of multiple S3 buckets, which will expose your sensitive data stored in this bucket. Let’s walk through the difference between creating an S3 bucket through the console versus using Terraform.
Creating an S3 Bucket Manually (Console Method) – Risk of Misconfiguration
Step 1: Log in to the AWS Console
Go to the S3 service and click on ‘Create bucket’.
Step 2: Name the Bucket
Enter a bucket name (e.g., ‘terrateam-sensitive-data’) and select your region.
Step 3: Permissions
While creating the bucket, if left unnoticed, you might disable the ‘Block all public access’, leaving the bucket open to the public.
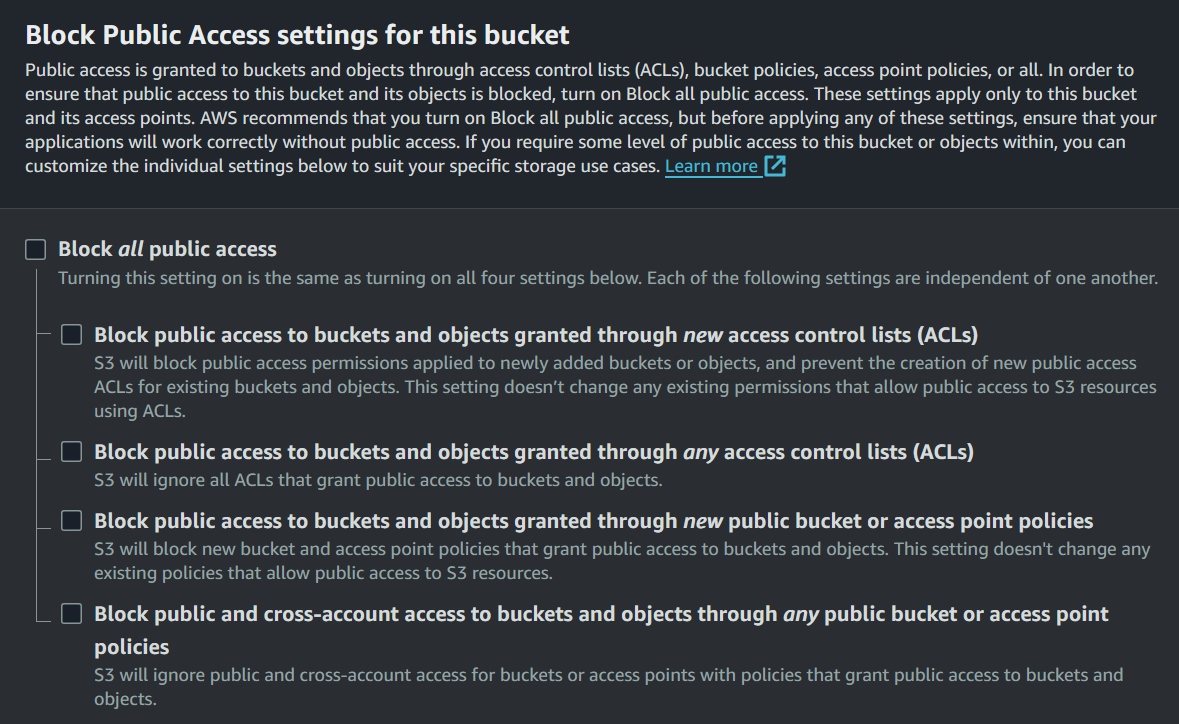
Step 4: Create the Bucket
Complete the setup to deploy your S3 bucket.
Now, this bucket is at risk of being accessed by anyone, exposing sensitive data storage and information in the bucket, which can lead to a data breach.
Using IaC to Securely Create the S3 Bucket
By using Terraform as IaC for creating the same bucket, we can make sure that our S3 bucket is always private by default by simply following these steps:
Step 1: Create a main.tf file
First, create a new file named main.tf. This file will contain the S3 bucket Terraform configuration code, as shown below:
In this code, the [.code]provider "aws"[.code] block sets up AWS as the service provider in the [.code]us-east-1[.code] region. The [.code]aws_s3_bucket[.code] resource creates the S3 bucket named ‘firefly-dash-bucket’. Lastly, the [.code]aws_s3_bucket_public_access_block[.code] further makes sure that the bucket is private by blocking all public access settings.
Step 2: Initialize Terraform
Run the [.code]terraform init[.code] command to initialize Terraform, set up your working directory, and download the necessary AWS provider plugin.
Step 3: Apply the Configuration
After initialization is complete, deploy your S3 bucket with [.code]terraform apply[.code] command. Terraform will give you an output with the changes. Review these changes to make sure everything looks correct according to what we have planned in the code.
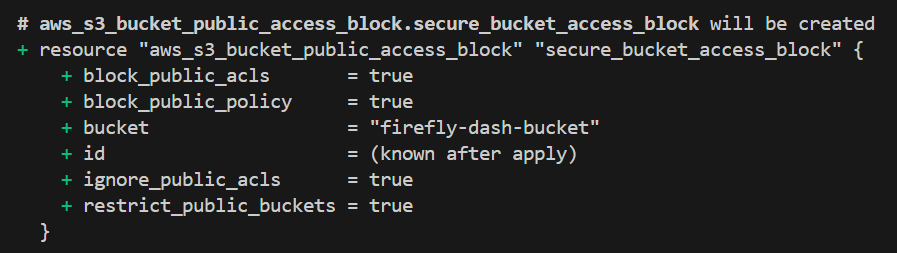
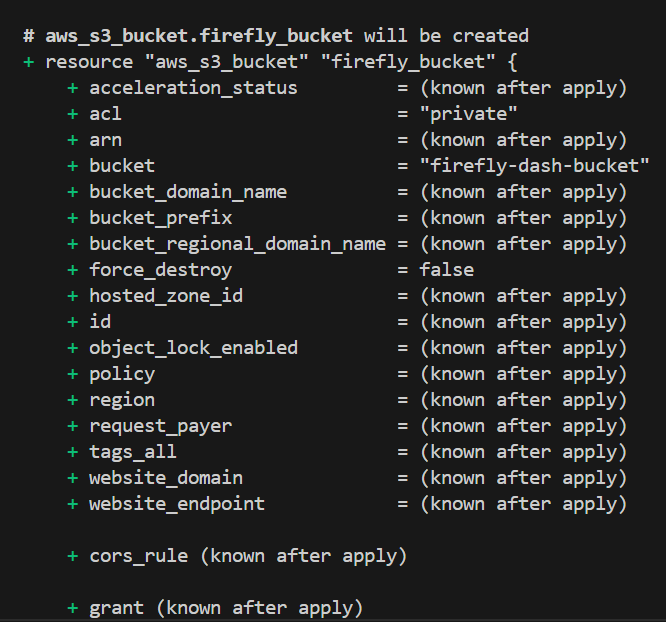
By following these steps, you’ve created an S3 bucket with private access using Terraform by default and protected from any public access. This process of creating the S3 bucket through Terraform makes sure that the bucket’s security settings are always correctly applied, which reduces the risk of misconfiguration.
Securing Open Ports with IaC
As we have already discussed earlier, one of the common security risks in the cloud is leaving unnecessary ports open, which can allow unwanted access to your servers. This makes it easier for attackers to exploit open ports and gain unauthorized access to your infrastructure.
With IaC, we can control exactly which ports should be open or closed, making sure that only the required ports are accessible, and reducing the chance of unauthorized access.
In this example, we’ll create an AWS EC2 virtual machine using Terraform with a security group that only allows traffic through ports 80 (HTTP) and 443 (HTTPS), simply blocking all other unnecessary ports and keeping your instance more secure.
Step 1: Create the Terraform Configuration
Create a main.tf file. Here, configure your security group and attach it to an EC2 instance:
In this code:
- The [.code]aws_security_group[.code] resource creates a security group named [.code]firefly-web-sg[.code] that allows only HTTP (port 80) and HTTPS (port 443) traffic. All other ports are blocked by default, making sure that the EC2 instance is protected.
- The [.code]aws_instance[.code] resource creates an EC2 instance and assigns the security group to it, ensuring only traffic on ports 80 and 443 is allowed.
Step 2: Initialize and Apply Terraform Configuration
Initialize and apply your infrastructure configuration with [.code]terraform init[.code] and
[.code]terraform apply[.code] command.
Now, after running this command, Terraform will create the EC2 instance with the security group that only allows traffic through ports 80 and 443.

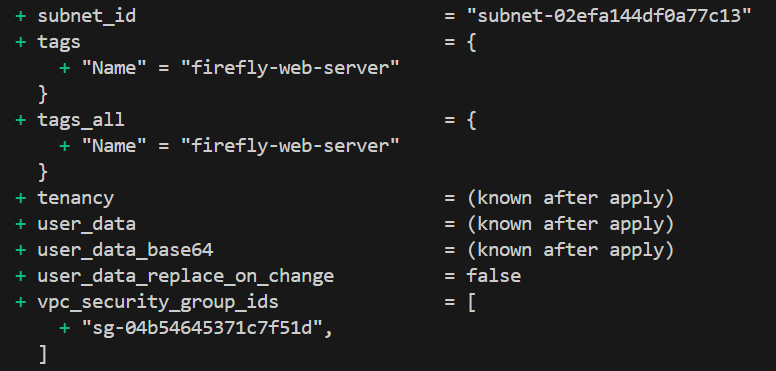
As CISO, you can create, implement, and enforce such security policies to secure your infrastructure.
Ensuring Data Encryption with IaC
Without encryption, your data can be read by anyone with access permission, which leads to a severe data breach. With IaC, we can make sure that encryption is always enabled for all our cloud resources, such as S3 buckets, to keep data secure throughout.
In this example, we'll use Terraform to create an AWS S3 bucket with server-side encryption enabled by default. This means that all the data that is stored in the bucket will be encrypted automatically, making sure that it remains protected.
Step 1: Create the Terraform Configuration
Let’s start by creating a main.tf file and defining the [.code]aws_s3_bucket[.code]:
In this code, [.code]aws_s3_bucket[.code] resource creates an S3 bucket named [.code]firefly-secure-bucket[.code] with the [.code]server_side_encryption_configuration[.code] block that ensures that all the data that is stored in this bucket will be encrypted using the AES256 algorithm.
Step 2: Initialize and Apply Terraform Configuration
Run the [.code]terraform init[.code] command to initialize the Terraform and [.code]terraform apply[.code] command to create the bucket with encryption enabled.
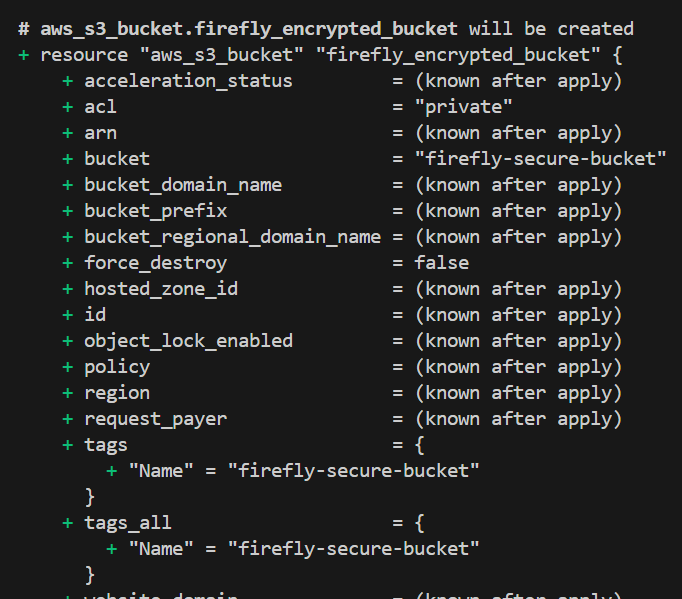
By using IaC with Terraform, we’ve ensured that any data that is stored in this S3 bucket will always be encrypted, protecting it from unauthorized access and keeping your cloud environment more secure.
Using IaC to Master Infrastructure Security with Firefly
So far, we’ve seen how challenging it can be for a CISO to handle cloud infrastructure and how they can use the IaC tools, like Terraform, to take care of permissions, access, and encryptions.
Now, how do you continuously monitor it and ensure that your infrastructure continues to be secure from any infrastructure security attacks as it grows?
Firefly can make things much easier, offering a clear, centralized platform that simplifies tracking, managing, and making your cloud environment more secure.
Centralized Dashboard
Firefly provides a centralized dashboard that gives you an overview of your entire cloud infrastructure in one place for various cloud providers, such as AWS, Azure, and GCP, making it much easier to find issues and take action that are manual or recommended.
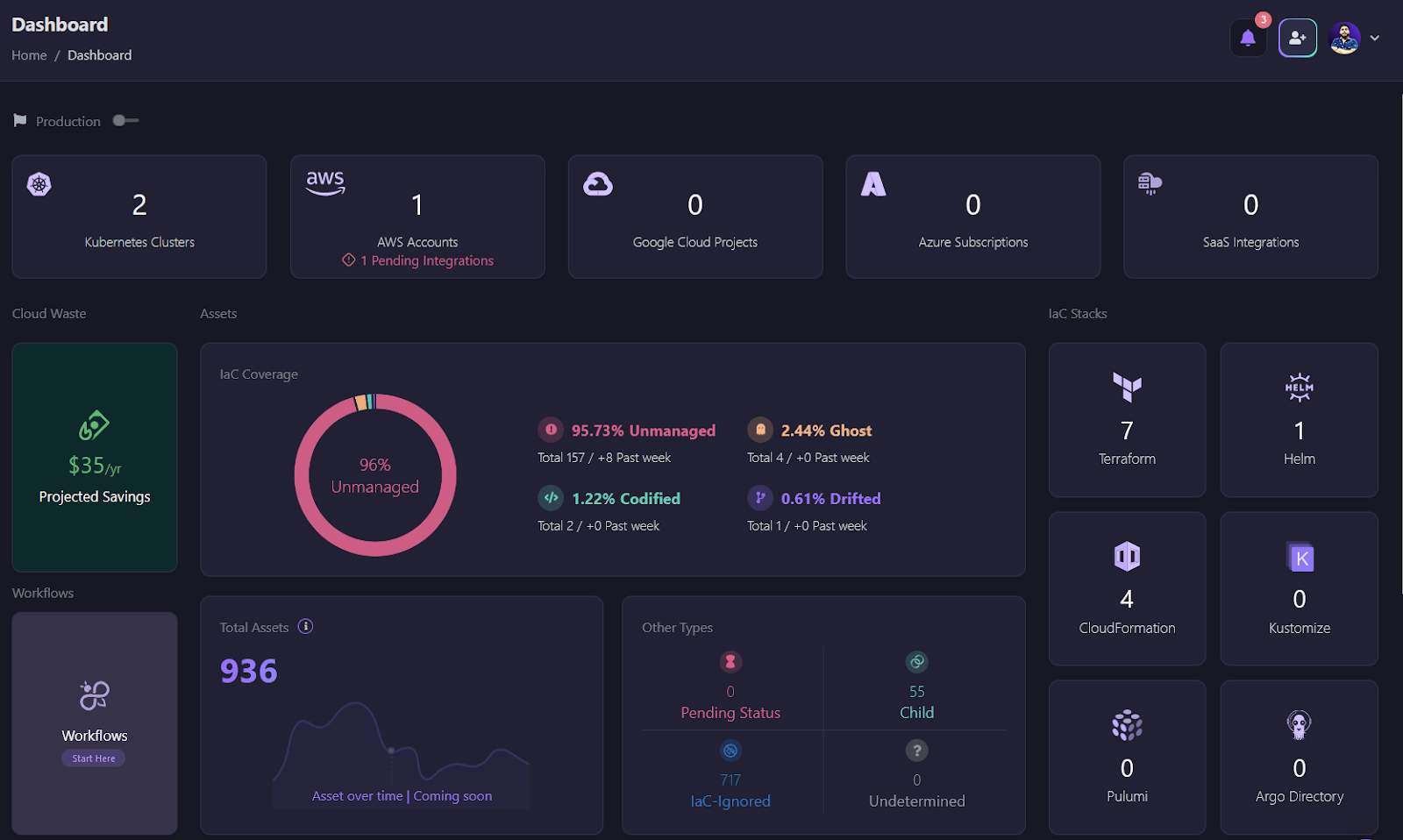
The dashboard shows all the key metrics that are important for a CISO to monitor, such as:
- Unmanaged Resources: These are cloud resources that aren’t managed by IaC, which means they might not follow the organization’s security policies.
- Ghost Resources: Ghost resources are those assets or resources that exist in your cloud environment but aren’t tracked or defined by IaC. They can pose security risks since they aren’t governed by your security configurations.
- Codified Resources: These are resources that are properly managed by IaC, making sure that they follow the security best practices and configurations.
- Drifted Resources: Drifted resources are those that have changed from their original IaC settings, which can simply lead to security vulnerabilities or misconfigurations if not corrected.
This makes it much easier to maintain control over your cloud environment and ensure that every resource aligns with your organization's security standards.
Firefly Workflows
Firefly Workflows make it much easier to automate tasks in your cloud setup by connecting with CI/CD pipelines. This helps in keeping your cloud infrastructure more secure and in line with the organization's rules and compliance.
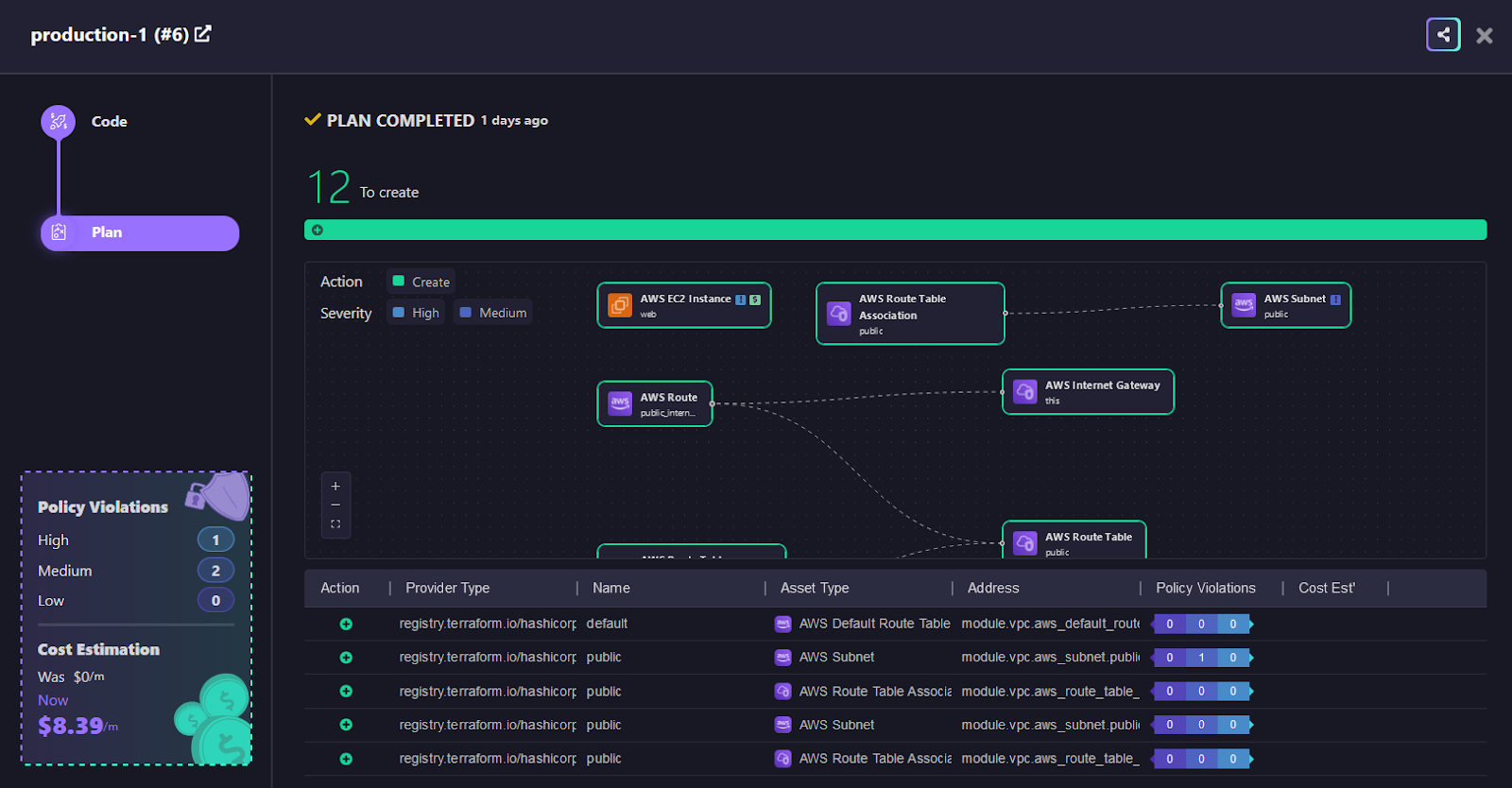
The visual layout of the workflow shows the Terraform plan output with all the AWS resources that will be created, like EC2 Instances, Subnets, and Route Tables. You can see and understand how every resource depends on each other. It also displays any policy violations that might be deployed while deploying these resources, which is essential to prevent any cloud security breaches.
Firefly Workflows spotted a few policy issues in real-time, helping avoid security risks before they are deployed, like an AWS EC2 Instance missing [.code]associate_public_ip_address[.code]. This was marked as a high-risk the problem, showing how Firefly can quickly catch these security gaps before it goes into your cloud environment, such as production.

Firefly Workflows not only spot issues but also help you manage costs and keep your cloud setup more secure and well-organized. Firefly gives clear cost estimates, showing how cost-effective infrastructure management can be, with this instance costing $8.39 per month, including $7.59 for instance usage and $0.05 for vCPU hours. This helps you keep an eye on expenses and manage your budget better.
Guardrails
Firefly Guardrails act as safety rules to make sure that your cloud configurations remain secure and compliant with your organization’s policies. By setting up Guardrails within Firefly, you can define specific policies that all your cloud resources must follow. If any policy violations are detected, Firefly automatically blocks these changes, making sure that your cloud environment stays within the set security standards.
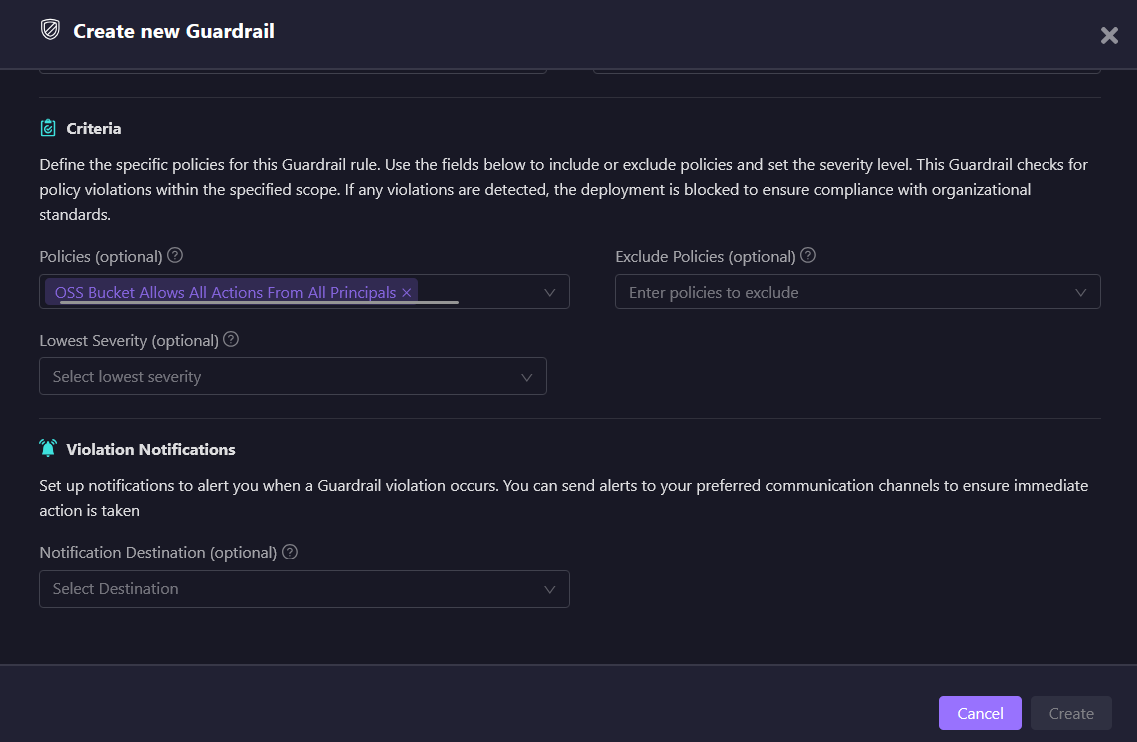
Let’s say a guardrail was created to monitor policies such as ‘S3 Bucket Allows All Actions From All Principals’. This will make sure that if any S3 bucket permissions are too open, Firefly catches it and prevents the deployment from proceeding until the issue is fixed.
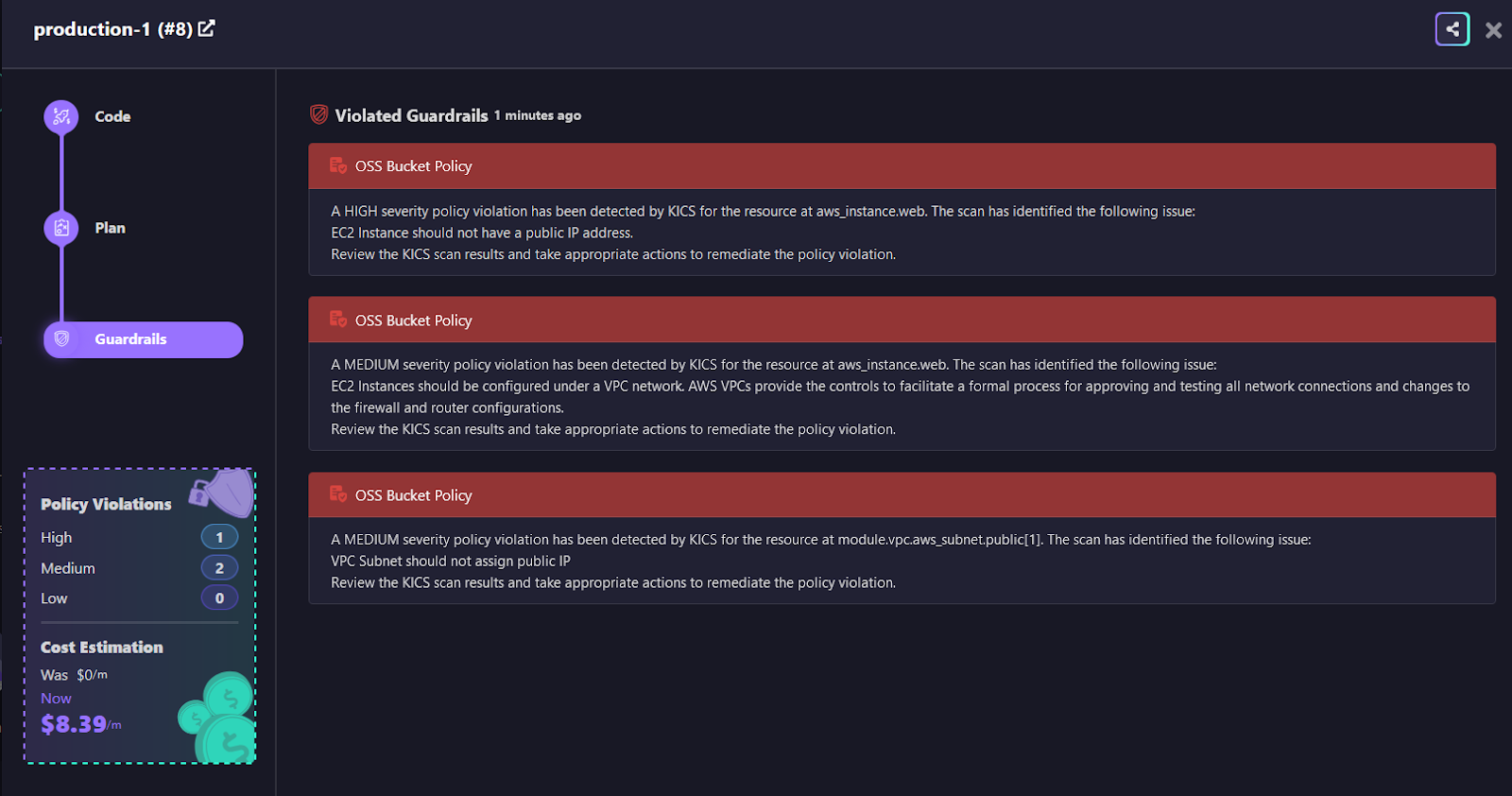
Here, several Guardrails violations were detected. The system flagged these issues with different severity levels, such as High and Medium, making it much clearer which ones require immediate attention. One high-severity issue detected was that the AWS EC2 Instance had a public IP address, which goes against secure practices.
This Guardrail feature is powerful as it can automatically block your CI/CD pipeline if any violations are found, making sure that insecure changes never reach your cloud environment until they are resolved. This approach helps in maintaining a secure and compliant cloud infrastructure at all times.
Firefly Guardrails also offer the option to send violation notifications through Slack or Email, so you can quickly be alerted when a policy is breached by anyone in the team. This makes it easy to respond to security issues before they cause any harm.
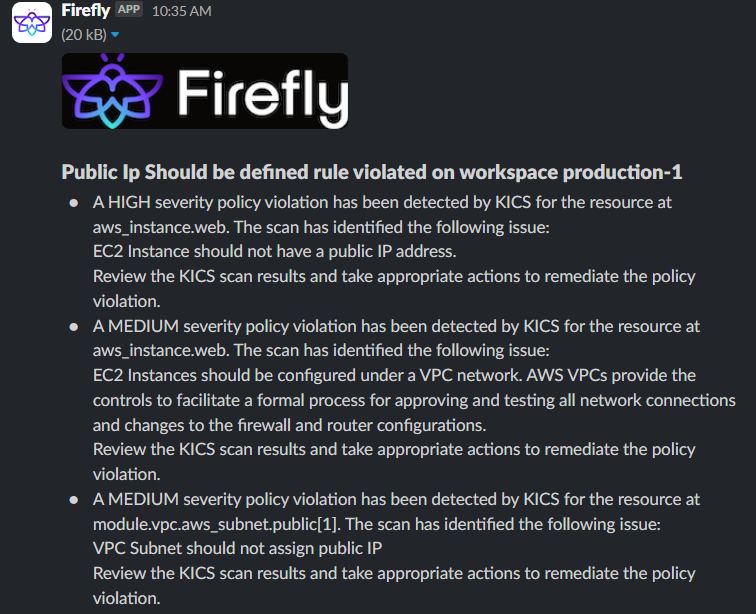
All in all, Firefly gives CISOs a clear view of cloud resources, quickly finding security problems, and making sure everything stays safe and follows the rules. Its easy-to-use dashboard, automatic workflows, and guardrails help CISOs manage infrastructure security better and avoid mistakes. This means they can spend less on monitoring and reviewing your infrastructure.


